The Latest Strategies from Australian CISOs You Can Implement Today
Discover cyber security insights from Australian CIOs gathered from ADAPT Security Edge 2023 events on building a resilient culture, crisis preparation, and risk management for a distributed workforce.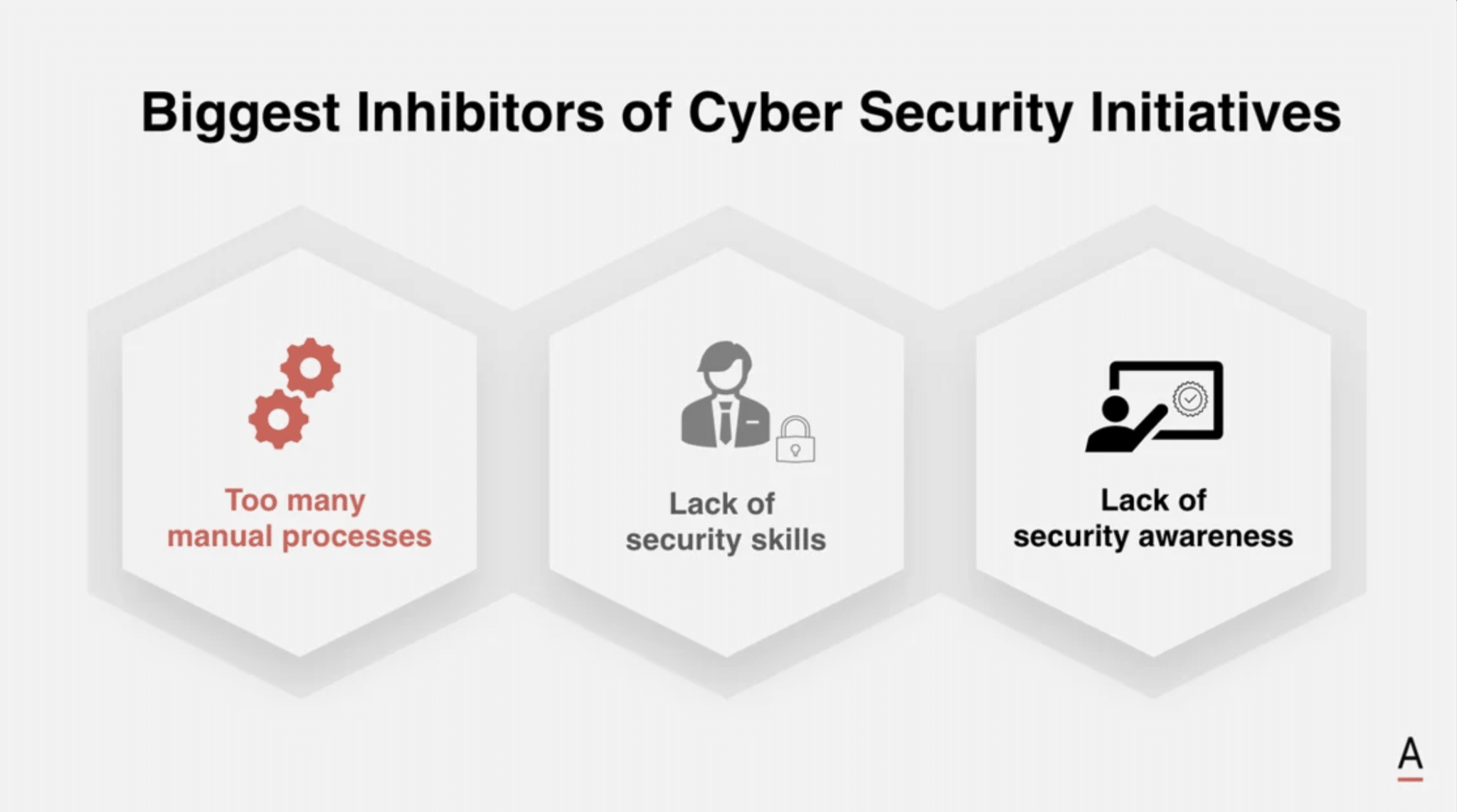
A surge in cyber threats challenges Australian organisations, leading to an urgent call for proactive cyber security measures.
ADAPT Security Edge conferences in 2023 gathered executive leaders and experts to address these challenges head-on.
We delve into the insights and solutions they offered to empower Australian organisations in enhancing their cyber security measures, particularly focusing on the perspectives and strategies of Australian CISOs.
From the necessity of risk assessments to innovative strategies, we explore the key elements shaping Australia’s renewed focus on cyber resilience.
Together with cyber security experts, ADAPT looks into themes such as unified cyber defense strategies, Zero Trust security principles, upskilling for resilience, and national strategies for sustainable cyber security.
Explore firsthand insights and strategies from Australian CISOs defining the nation’s response to the region’s most urgent cyber security challenges.
Challenges
Tackling a 13% Surge in Cyber Security Threats
Australian organisations are facing an escalating threat of cybercrime, evidenced by the substantial 13% increase in reports received by the Australian Cyber Security Centre (ACSC), reaching 76,000 cases compared to the previous financial year.
This surge, equating to a report every 7 minutes, underscores the pressing need for a proactive and robust approach to cyber security.
In response to this alarming trend, organisations must conduct comprehensive risk assessments and implement preemptive measures to mitigate the impact of cybercrime.
Figures accentuate the urgency of building a resilient culture capable of withstanding operational stresses, cyber-attacks, and other looming threats.
ADAPT Security Edge conference in April 2023 provided critical Australian CISO insights on security strategy based on detailed surveys of Australian executive leaders.
The event centred on the “Crisis Preparation, Risk, Culture, and Operational Resilience” theme, featuring contributions from 27 experts, 18 keynotes and panels, and 27 strategic partners representing organisations safeguarding almost a quarter of Australia’s GDP.

As breach frequency rises, Australian CISOs strategically prioritise security and resilience in the coming 12 months.
With one in four Australian businesses experiencing breaches weekly, CISOs focus on building secure and trusted organisations, improving resilience against operational and market-based risks, and enhancing operational effectiveness.
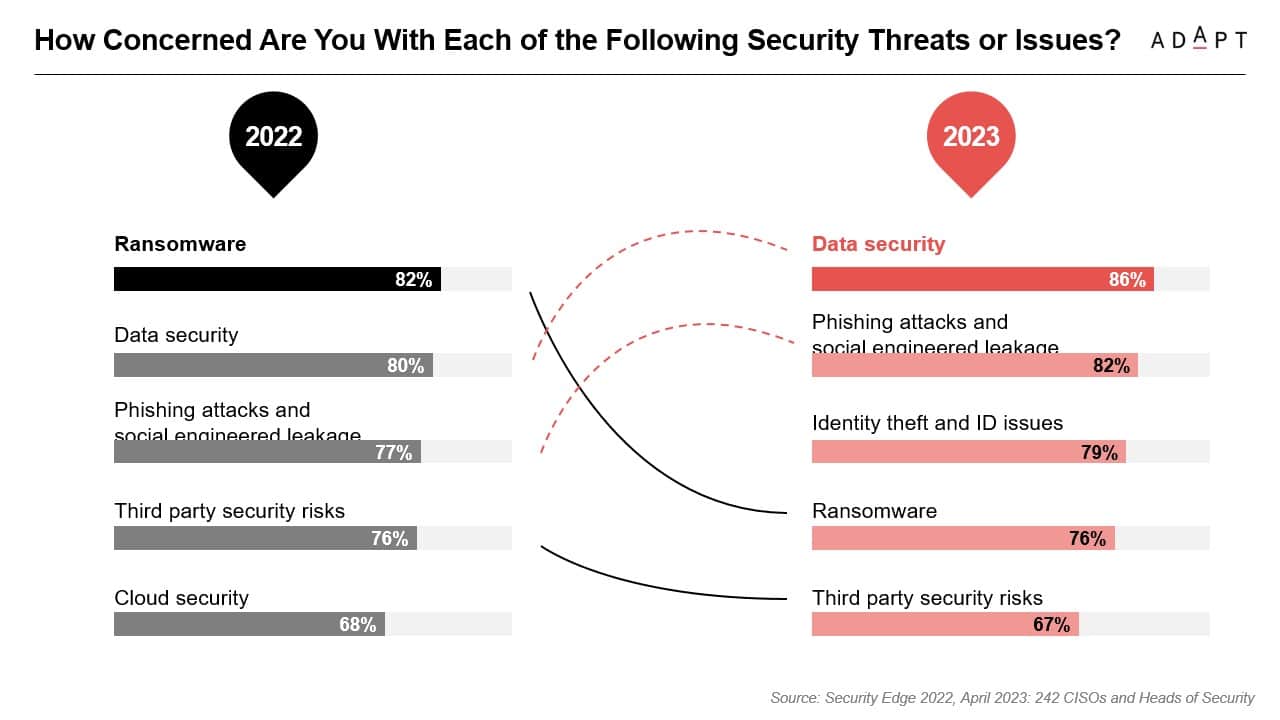
While 62% of CISOs say they are cyber resilient, data security still emerges as the primary concern for CISOs and Heads of Security in the next 12 months, with 86% expressing worry.
This is closely followed by concerns about leakage through phishing attacks and social engineering at 82%.
Other notable concerns include identity theft and ID issues at 79%, ransomware at 76%, and third-party security risks at 67%.
Examining business and technical inhibitors, a need for more budget and legacy systems takes the lead in impeding security initiatives in 2023.
A survey of over 250 Australian CISOs and Heads of Security revealed challenges such as budget allocation constraints, too many manual processes, lack of in-house security skills, and the rapid evolution of security threats.
On the technical front, challenges include:
- Legacy systems and processes
- Technology stack complexity
- Lack of data ownership policies
- Issues with identity and access management tools and policies
The cyber security landscape in Australia and New Zealand is undergoing a profound transformation due to the escalating wave of cyber threats, as discussed at ADAPT Security Edge 2023.
Financial services organisations, exemplified by Mercer Pacific, are particularly grappling with challenges amid a surge in cyberattacks.
Stricter government regulations and hefty fines of up to $50 million for data breaches underscore the critical need for organisations to fortify their cyber security measures, prioritising data protection to maintain customer trust and operational integrity amid the growing cyber risks
In summary, Australia’s escalating cyber threat landscape necessitates a proactive and comprehensive approach to cyber security.
ADAPT Security Edge conference highlighted crucial insights and spotlighted the strategic priorities of CISOs in the face of increasing breach frequency.
Priorities
CISOs and CFOs Align for Stronger Cyber Resilience
Australia’s escalating cyber threat landscape necessitates a unified and proactive approach to cyber security.
Insights from the ADAPT Security Edge 2023 conference highlight the strategic priorities Australian CISOs identified in response to increased breaches.
At the forefront of CISO priorities are initiatives to prevent brand damage and data loss, ensure data privacy, secure end-users, and foster customer trust and retention.
These priorities recognise the urgent need to strengthen defences against the nation’s evolving cyber threats.
Prof. Lesley Seebeck, Chair of the National Institute of Strategic Resilience and Chief Executive at Cyber 21, emphasises cyber resilience and aligns with the broader concerns expressed by CISOs.
She supports her stance with evidence of cyber threats’ surging frequency and sophistication.
Prof. Lesley advocates for a comprehensive approach, drawing attention to the importance of diverse perspectives in addressing the multifaceted nature of cyberattacks.
Her focus on early threat detection, strategic planning, and collaborative responses dovetails with the proactive stance urged by CISOs.
83 CFOs and Heads of Finance, as revealed in ADAPT’s survey, echo these sentiments by allocating budget priorities that align with the cyber security concerns outlined by CISOs.
Managing risk and cyber security stands out as the top priority, indicating a financial sector cognisant of cyber security’s pivotal role in organisational resilience and risk management.
These sections work together to present a unified narrative. CISOs recognise the imperative need for cyber resilience, supported by the evidence from Prof. Lesley Seebeck.
The financial sector’s budget priorities align with this need, and together, they call for a proactive and comprehensive approach to address Australia’s cyber security challenges.
Solutions
Embrace Zero Trust Security for Cyber Resilience
Amidst the ever-evolving landscape of Australian cyber security, a strategic approach emerges, subtly interweaving key components to bolster the nation’s digital resilience.
At the forefront is the focus on fostering digital trust, a concept championed by The Hon Victor Dominello, Director UNSW/UTS Trustworthy Digital Society Hub, Tech Council of Australia Board Member and Former Minister for Customer Service and Digital Govt and Founder of ServiceGen.
This revolves around digital identity and trust architecture, underscoring the foundational role of trust in the vast digital ecosystem.
As individuals increasingly integrate technology into their lives, preserving trust, privacy, and security takes centre stage.
Building upon this ethos, Herb Kelsey, Project Fort Zero Team Lead at Dell Technologies, advocates a nuanced implementation of a Zero Trust architecture.
This approach explained at ADAPT Security Edge 2023, extends security measures to users and devices, prioritising authentication and compliance with stringent policies.
By treating user and device identities as a unified entity across the network, Zero Trust signifies a fundamental shift in security practices, addressing the evolving cyber threat landscape and safeguarding valuable data and AI models.
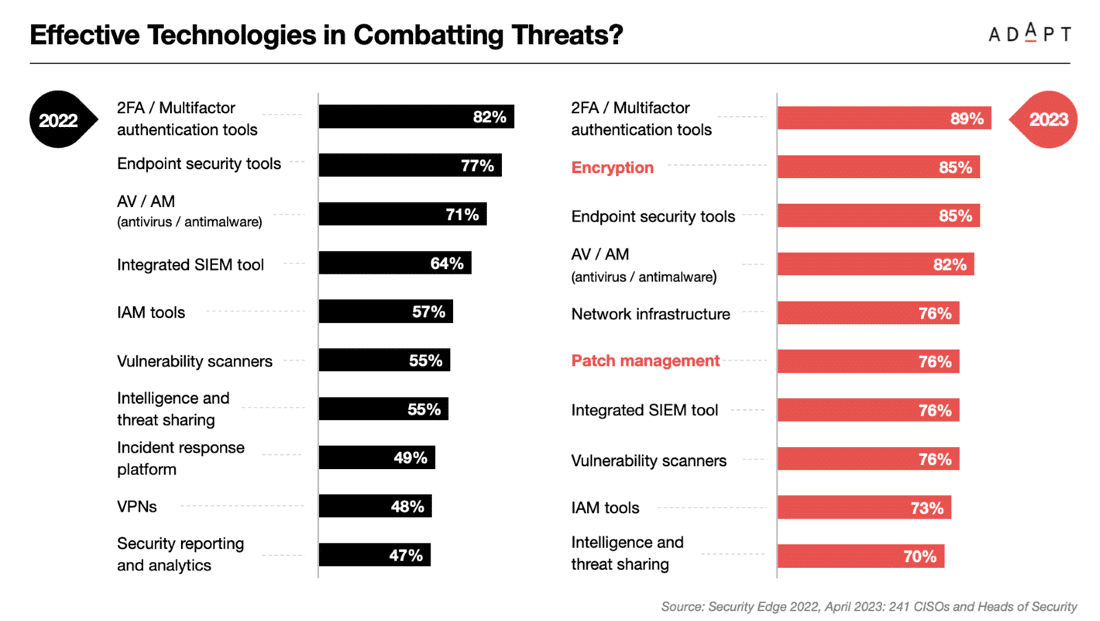
In harmony with the Zero Trust philosophy, Australian Chief Information Security Officers (CISOs) and Security Heads subtly endorse multifactor authentication tools as their preferred choice in countering cyber threats
Recognising the inherent vulnerability in human-operated systems, 89% of professionals prioritise 2FA/Multifactor authentication tools.
This seamless alignment with Zero Trust principles acknowledges the critical role of mitigating risks associated with human factors.
The narrative unfolds further in a cyber security panel at ADAPT Security Edge, where experts such as Peter Hind, Bianca Wirth, Jean Baptiste-Bres, and Francis Ofungwu convene to discuss challenges and solutions in Australian cyber security.
Focusing on the proliferation of endpoints, supply chain vulnerabilities, and the need for a holistic security approach, the panel subtly underscores the imperative of Zero Trust within a robust security framework.
The challenges of implementing solutions across diverse organisational departments are explored, shedding light on the scale of the issue with numerous people, agencies, devices, and legacy applications.
The panel calls for improved metrics at all organisational levels, subtly advocating for a secure development life cycle and reinforcing the interconnected nature of these cyber security strategies.
In a final layer of support, the session subtly stresses the importance of understanding security needs beyond technological solutions.
Boards and executive committees are urged to act proactively on reports; caution is advised in implementing artificial intelligence.
This aligns with the overarching theme of trust, subtly emphasising transparency, privacy compliance, and the strategic deployment of AI to solve genuine issues.
The narrative unfolds as a symphony of interconnected strategies, subtly moving from fostering digital trust to implementing Zero Trust architectures and prioritising multifactor authentication.
These elements harmonise organically to create a robust defence against the evolving threats in Australia’s digital landscape, subtly underlining the importance of a unified and comprehensive approach to cyber security.
Watch the full panel discussion with security leaders from the NSW Department of Planning, HSBC, and GitLab.
Fortify Email Security Against Ransomware Threats
Marco Figueroa discussed the critical nature of email-based cyberattacks, specifically the deployment of ransomware through email at ADAPT Security Edge 2023
This insight is substantiated by Australian Institute of Company Directors’s Senior Manager for Cyber Security, Risk and Compliance Marco Figueroa’s statement that email serves as the primary threat vector across various industries.
He emphasises that these attacks often occur when individuals are less vigilant, such as during long weekends or holidays.
As Marco puts it,
The biggest threat for any organisation, large or small, regardless of their industry, is email, is the email thread.”
This key point underscores the necessity of implementing robust email security measures and automation to effectively prevent and respond to threats from emails.
It serves as a reminder of the continuous vigilance required to combat these cyber threats.
It highlights the significance of being well-prepared with clear incident response plans and effective communication, both within the organisation and externally.
Defend, Collaborate, and Integrate Culturally for a Unified Cyber security
Experts unanimously advocate for a collaborative defence strategy in the dynamic landscape of Australian cyber security.
At the forefront of this approach is a collective understanding of individual roles within organisations, stressed the need for comprehensive training in security best practices.
This foundational knowledge creates a resilient workforce capable of effectively countering cyber threats.
As pointed out by Anafrid Bennett, Head of Tech Security and Property at Greater Western Water, bolstering this collective defence is collaborative threat-sharing and intelligence-sharing platforms.
These platforms serve as the connective tissue of Australia’s cyber security community, enabling real-time detection and response to evolving threats.
The collective intelligence shared within these platforms accelerates incident response and fosters a culture of continuous learning, minimising the impact of cyberattacks.
Complementing this collaborative defence strategy focuses on behavioural and cultural dimensions of risk management.
ADAPT’s Principal Research Analyst, Peter Hind and Tamara Scicluna, Executive Director and Co-founder at Rhizome Advisory Group assert that effective risk management transcends compliance, stressing the integration of policies into daily operations.
This holistic understanding of organisational behaviour ensures that cyber security policies are not just written guidelines but integral components of the day-to-day decision-making fabric within organisations.
As the collective defence strategy takes shape, the importance of community strength becomes evident.
In the cyber security landscape of Telstra, building a robust network and community is considered a pillar of resilience.
This interconnected network acts as a collective intelligence hub, providing early warnings, fostering resource sharing, and supporting professionals through peer interactions.
The diverse perspectives within this community drive innovation and contribute to the collective ability to influence and shape cyber security policies and standards.
Underlying this collaborative defence is the imperative to empower cyber skills and sovereign capabilities.
Cyber security leaders Kylie Watson, Tom Kenyon, and Alan Marjun highlight the need to address the persistent cyber skills shortage by mobilising talent and focusing on education, particularly mathematics and science.
This investment in human capital, coupled with a comprehensive national strategy, ensures the sustainability of Australia’s cyber security posture, safeguarding critical infrastructure and fostering resilience against emerging threats.
In summary, the interconnected threads of collective defence, collaborative platforms, behavioural focus, community strength, and skills empowerment form a cohesive fabric of cyber security resilience in Australia.
Each element reinforces the other, creating a symbiotic relationship that strengthens the nation’s ability to navigate the evolving cyber landscape.
Conclusion
Australia faces a notable surge in cyber threats.
Challenges, ranging from technical hurdles to evolving risks, underscore the need for a collective response.
CISO priorities, echoed by Prof. Lesley Seebeck and executive leaders, pointed out the importance of resilience and collaboration.
This narrative encourages a measured, cooperative, and comprehensive approach to strengthening Australia’s cyber security defences amid the growing threat landscape.