What We Learnt About Crisis Preparation and a Resilient Risk Culture at Security Edge
Discover insights from the ADAPT Security Edge event on building a resilient culture, crisis preparation, and risk management for a distributed workforce.
Organisations face a growing range of risks that can trigger crises.
The Australian Cyber Security Centre (ACSC), has been inundated with an alarming surge of cybercrime reports, totalling 76,000 cases.
This marks a significant spike of almost 13% compared to the preceding financial year, indicating an unabated rise in cybercrime activities.
With one report received every 7 minutes, up from every 8 minutes last year, the figures speak for themselves. These alarming statistics underscore the pressing need for robust cyber security measures and a proactive approach to address these rampant threats.
To minimise the impact of cybercrime, it is essential to conduct risk assessments and take pre-emptive measures.
Organisations must respond quickly and effectively to crises by guiding stakeholders.
Building a resilient culture requires designing processes and response plans to withstand operational stresses, cyber-attacks, and other threats.
Investing in crisis preparation and risk management safeguards an organisation’s reputation, business continuity and stakeholder interests, enabling it to thrive in an uncertain world.

ADAPT Security Edge: Key Insights on Security Strategy
ADAPT Security Edge, April 2023, presented insights from over 1,000 detailed surveys of Australian executive leaders, featuring 27 experts, 18 keynotes and panels, and 27 strategic partners.
Attendees represented organisations protecting almost a quarter of Australia’s GDP.
The key theme of the event was “Crisis Preparation, Risk, Culture and Operational Resilience.”
The core findings focused on security strategy, investment priorities, resource allocation, and the unique challenges facing Australian CISOs.
- Australian businesses facing increasing breach frequency, CISOs prioritise security and resilience in next 12 months.
1 in 4 Australian businesses have experienced a breach, which used to happen every quarter but now occurs weekly. Given this threat, it comes as no surprise that Australian CISOs top business priorities in the next 12 months are:
-
- Building a secure and trusted organisation.
- Improving resilience against operational and market-based risks.
- Improving operational effectiveness.
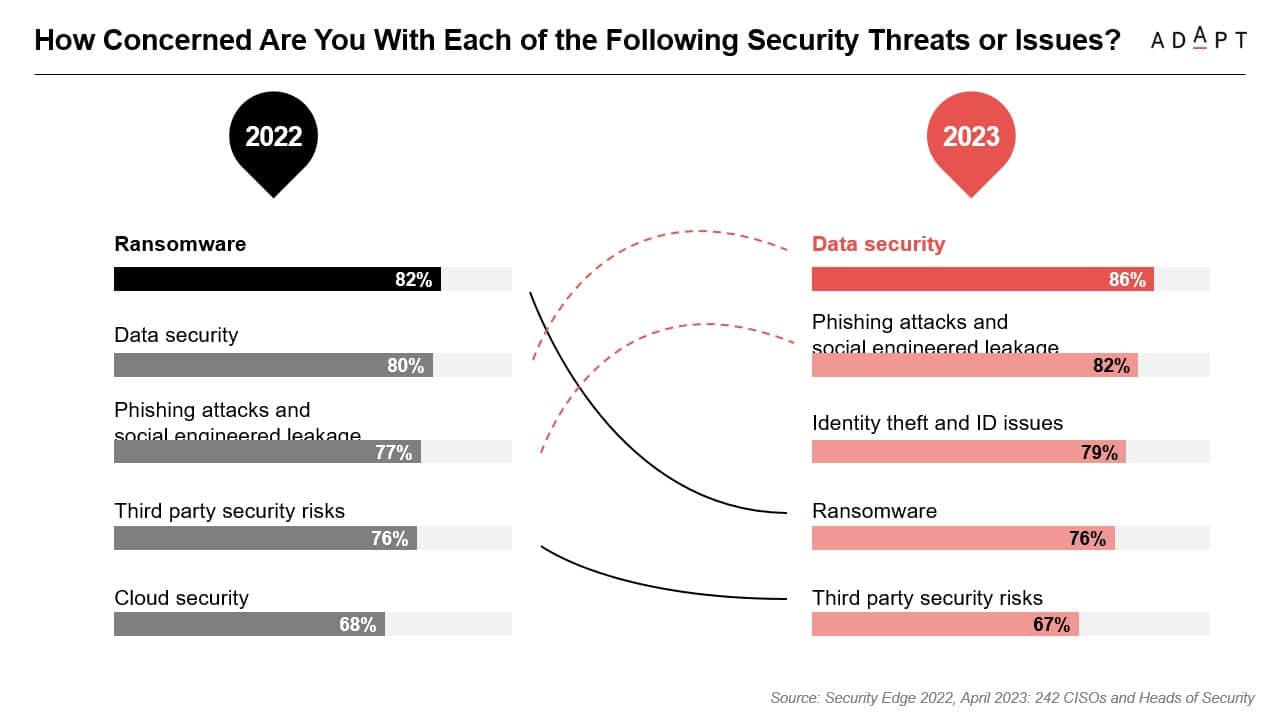
- CISOs and Heads of Security are most concerned about data security for the next 12 months.
In a recent survey, involving 242 CISOs and Heads of Security, ADAPT asked, “How concerned are you with each of the following security threats or issues? Data security topped these concerns, followed by leakage via phishing attacks and social engineering came a close second.
-
- Data security – 86%
- Phishing attacks and social engineered leakage – 82%
- Identity theft and ID issues – 79%
- Ransomware – 76%
- Third party security risks – 67%
- CISOs and Heads of Security prioritise preventing brand damage when it comes to security initiatives.
253 Australian CISOs and Heads of Security list the following as their most important drivers when planning and implementing security initiatives for the next 12 months:
-
- Preventing brand damage.
- Preventing data loss.
- Ensuring data privacy.
- Securing end-users.
- Customer trust/retention.
- Lack of budget and legacy systems tops both business and technical inhibitors for security initiatives in 2023.
In an ADAPT survey of more than 250 Australian CISOs and Heads of Security, the following factors were found to be the biggest business inhibitors to security initiatives this year:
-
- Lack of budget allocation.
- Too many manual processes.
- Lack of in-house security skills.
- Rapidly evolving security threats.
- Organisational culture and politics.
Below are the top technical inhibitors for security initiatives:
-
- Legacy systems and processes.
- Technology stack complexity.
- Lack of data ownership policies.
- Identity and access management tools and policies.
- Disparate security tools.
- Cyber security is top priority for CFOs and Heads of Finance.
ADAPT’s survey of 83 Australian CFOs and Heads of Finance revealed that the following are priorities for budget allocations for the remainder of the year:
-
- Managing risk and cyber security – 22%
- Digital workplace management – 18%
- IT – 14%
- Governance and compliance – 12%
- Employee wellbeing – 10%
- Business continuity planning – 10%
- Travel – 4%
- Real-estate – 2%
- R&D -1%
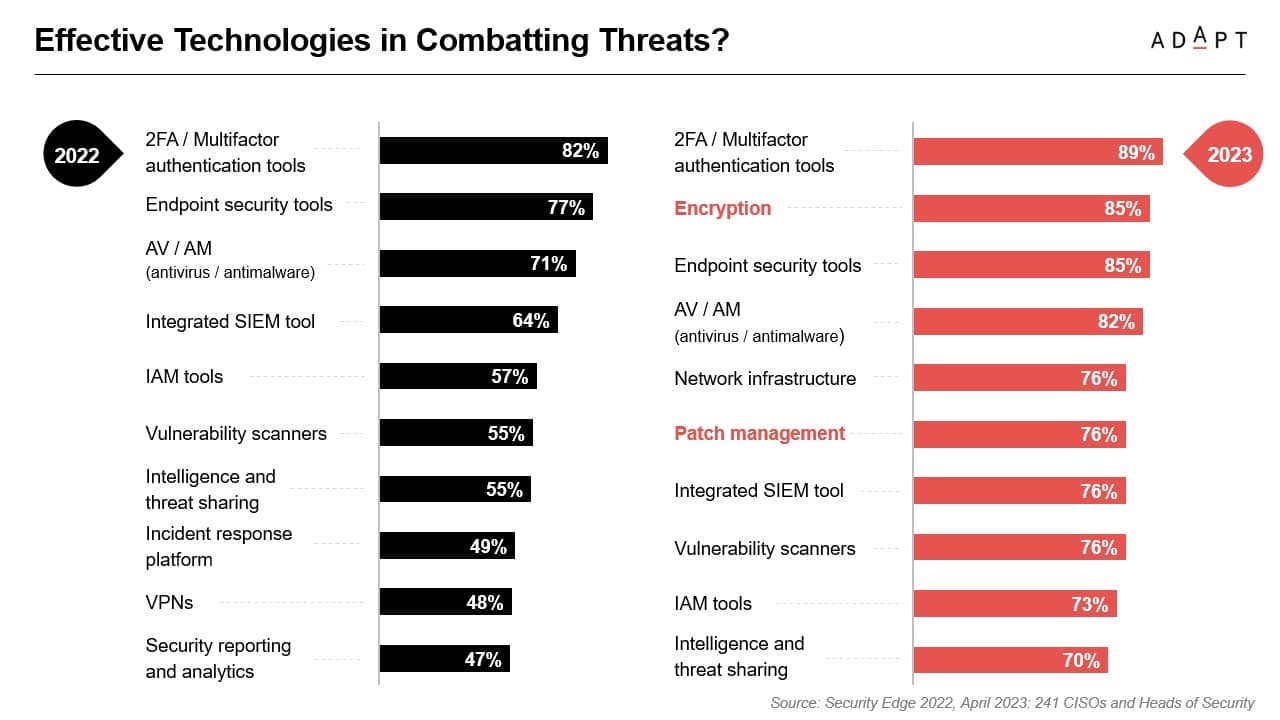
- Multifactor authentication tools are the top choice of Australian CISOs to defend against cyber threats.
When asked what the most effective technologies are to combat cyber threats in 2023, Australian CISOs and Security Heads listed:
-
- 2FA/Multifactor authentication tools – 89%
- Encryption – 85%
- Endpoint security tools – 85%
- AV/AM (antivirus/malware) – 82%
- Network Infrastructure – 76%
- Patch management – 76%
- Integrated SIEM tool – 76%
- Vulnerability scanners – 76%
- IAM tools – 73%
- Intelligence and threat sharing – 70%
Since multifactor authentication tools directly address the biggest security vulnerability – the people operating systems – they take the top spot. Kevin Mitnick, a world-famous hacker, and top cyber security speaker had this to say:
Companies spend millions of dollars on firewalls, encryption, and secure access devices and its money wasted because none of these measures address the weakest link in the security chain: the people who use, administer, operate and account for computer systems that contain protected information.”
Collective and Comprehensive: Experts emphasise the need for a collaborative approach to cyber security.
At the most recent ADAPT Security Edge, cyber security experts Kylie Watson, Alan Marjan, and Tom Kenyon discussed the need for a collective approach to security, emphasising the importance of individual roles in defending against cyber threats.
They also discussed specific concerns, including ransomware attacks and the threat of state-based actors.

By ensuring that all employees are trained in security best practices and investing in the latest security technologies, combined with strong leadership and governance, organisations can mitigate the impact of a ransomware attack and protect against state-based actors.
To prevent ransomware attacks, panellists recommended planning and exercising for scenarios, effective communication during cyber incidents, and limiting information sharing and network clean up.
Additionally, the importance of secure and trusted environments for data-driven goals was discussed, as well as cautioning against excessive data collection and emphasising appropriate treatment.
Watch the full panel discussion with security leaders from PwC, Australian Cyber Security Centre, and Internet 2.0.
Experts discuss Zero Trust and holistic security approach in cyber security panel.
In the same ADAPT Security Edge, a panel consisting of Peter Hind, Bianca Wirth, Jean Baptiste-Bres, and Francis Ofungwu, discussed various challenges in cyber security, including the proliferation of endpoints, supply chain vulnerabilities, and the panic buying of cyber security tools.
The panellists agreed that Zero Trust is essential for any security framework, and companies not implementing it are more exposed to threats. They also stressed the importance of a holistic security approach rather than relying on point solutions.
Zero Trust is a journey rather than a specific product or initiative. The panel suggested focusing on the secure development life cycle rather than any vulnerabilities.
It is essential to engage people across the organisation, such as developers, and recognise that cyber security is a team sport. Developers should be enabled to remediate vulnerabilities in real time within their development workflow.

The challenge of using niche solutions in different departments of a dispersed organization with core business systems was also discussed.
The panel described the scale of the challenge, which includes 16 to 17,000 people, 23 to 25 different agencies, around 100,000 devices, and a thousand applications, many of which are housed in legacy environments.
Additionally, metrics need to be improved at all levels of an organisation, including operations, management, and the executive.
Another highlight of the session was the need to understand what is needed in security rather than just relying on technological solutions.
The Board and executive committees must understand that protection is not limited to specific areas and must act on reports rather than just receiving them.
Security leaders must proceed with caution when implementing AI, ensuring the models used for training the AI are transparent, comply with privacy obligations, and help point AI towards real problems. In other words, AI should be used to solve current issues rather than simply making the wrong things more efficient.
Watch the full panel discussion with security leaders from NSW Department of Planning, HSBC, and GitLab.
Conclusion
To maintain digital growth and agility for a distributed workforce, organisations must build resilient cultures, ensure security, and ensure compliance.
This involves designing processes and response plans to withstand operational stresses, cyber-attacks, and other threats. This will support CISOs by improving risk culture and removing roadblocks to security success.
Organisations can safeguard their reputation, business continuity, and stakeholder interests by investing in crisis preparation and risk management, allowing them to thrive in an uncertain world.
























