How to sell to the Australian CISO
Discover how tech vendors can support Australian CISOs by addressing key challenges and providing strategic solutions to enhance cyber resilience and security.
Australian Chief Information Security Officers (CISOs) are facing a perfect storm of challenges: cyber threats are on the rise, resources are stretched thin, and government regulations are constantly evolving.
In this high-pressure environment, having a solid cybersecurity strategy is more important than ever.
A recent survey by ADAPT of 160 Australian CISOs revealed that their top priority is building a secure and trusted organisation.
They’re looking to strengthen their resilience against operational and market risks, improve security awareness, and find a balance between customer experience and robust privacy protection.
Their key focus areas include implementing automation technologies, streamli ning processes, and effectively managing operations and staff.
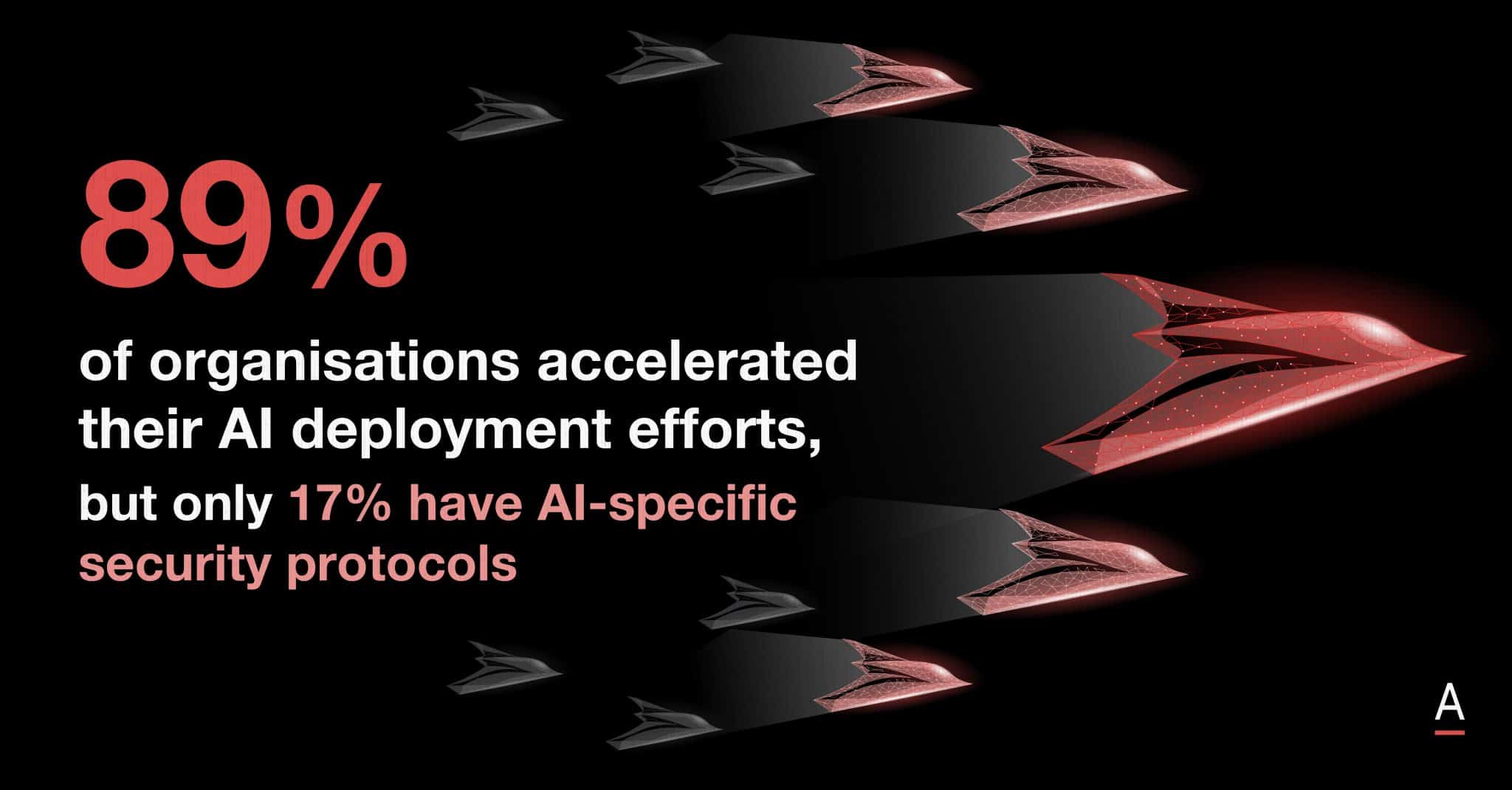
However, 89% of organisations have accelerated their AI deployment efforts, yet only 17% have implemented AI-specific security protocols, leaving gaps that attackers could exploit.
In this article, we’ll take a closer look at the many challenges Australian CISOs face and offer tech vendors practical advice on how they can lend a hand.
By tailoring how they present their solutions according to CISO priorities, vendors can play a vital role in helping CISOs navigate the complex regulatory, technological, and threat-based landscape.
Confronting resource constraints for Australian CISOs
Managing resource constraints
Australian Chief Information Security Officers (CISOs) are under-resourced and overworked.
66% of Australian CISOs report needing more resources to manage their workloads effectively.
ADAPT’s April 2024 Security Edge Insights found that, on average, they need a 41% increase in resources to meet current demands, with budgets often competing with AI investments.
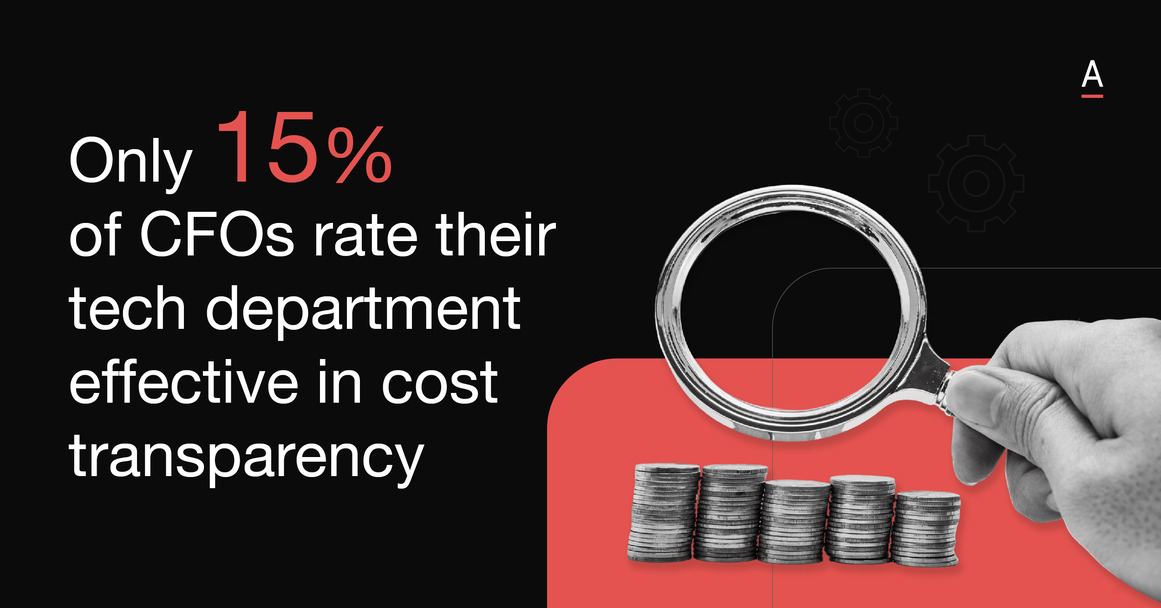
Despite growing AI adoption, data and security expertise are missing in over 80% of digital product teams, compounding the strain on security leaders who already face limited personnel and tools.

The rapid evolution of cyber threats puts CISOs under immense pressure to achieve more with fewer resources. Cyber criminals exploit these vulnerabilities, further stressing the need for adequate funding.
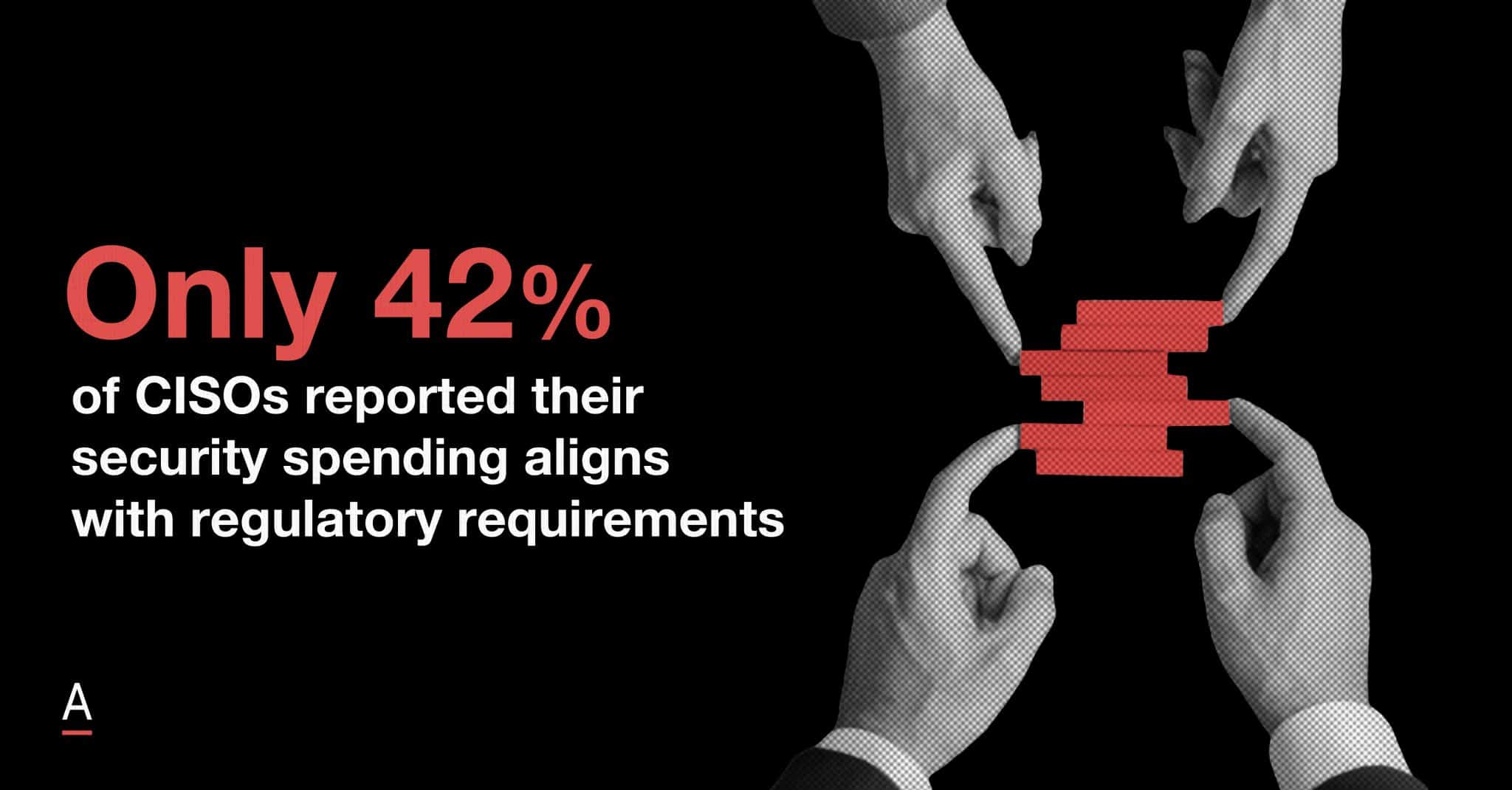
Yet, only 42% of CISOs reported that their security spending aligns with regulatory requirements, exposing organisations to significant compliance risks.
Top CISOs highlight the need for a 41% increase in resources to meet current demands.
This includes hiring more skilled personnel, investing in advanced security tools, and securing larger budgets.
These resources can enable CISOs to be proactive rather than constantly reacting to incidents, allowing them to strategically plan and strengthen their defences.
Cyber criminals exploit these vulnerabilities, further stressing the need for adequate resourcing.
The February 2024 Security Edge Survey highlighted that 70% of CIOs need a bigger budget allocation to deliver on the technology strategy.
Overcoming financial and technological barriers
Cyber crime costs the Australian economy $3.5 billion annually, with businesses spending an average of $276,000 to implement cyber security solutions.
Despite these costs, many organisations struggle to see the potential return on investment in cyber security.
CISOs must advocate for cyber security to be viewed as a critical investment rather than an expense, emphasising the long-term benefits of robust security measures.
By framing cyber security investments as essential for protecting assets and ensuring operational continuity, CISOs can better secure necessary funding.
Cloud adoption presents both opportunities and risks.
By 2025, 55% of workloads will reside on public cloud platforms, requiring a comprehensive security strategy to manage data protection, access controls, and compliance with industry standards.
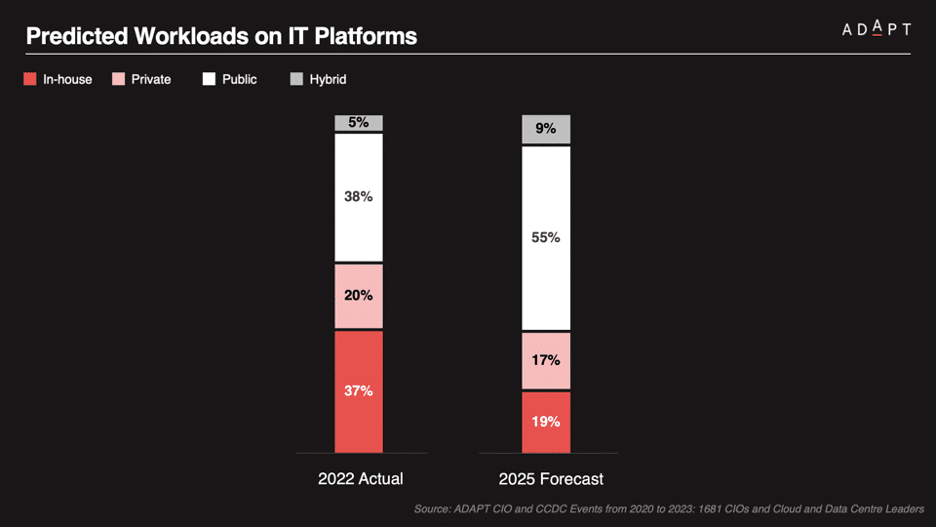
CISOs must balance the benefits of cloud computing with the need to mitigate associated risks.
Effective cloud security strategies prevent potential breaches and maintain data integrity, demonstrating the value of proactive measures in a cloud-first environment.
Legacy systems and outdated processes pose additional obstacles for CISOs.
Enhancing organisational communication and compliance
Effective communication between CISOs and executives remains a critical challenge.
Fewer than half of CISOs regularly update their leadership on security issues, resulting in a lack of prioritisation for cyber security at the highest levels.
Proactive engagement and continuous education for executives are essential to secure ongoing support for cyber security initiatives.
According to ADAPT’s Security Edge survey, 58% of organisations stress proactive executive involvement, and 74% identify ongoing education for executives as crucial for maintaining support.
Phishing and socially engineered attacks, followed by data security risks and third-party risks confronted CISOs the most in 2024.

These attacks exploit human vulnerabilities, highlighting the need for user education and advanced threat detection in a comprehensive security strategy.
Weekly breaches in one in four Australian businesses illustrate the pervasive nature of cyber threats.
Despite 64% of CISOs claiming cyber resilience, the frequency of breaches demands continuous improvement and vigilance.
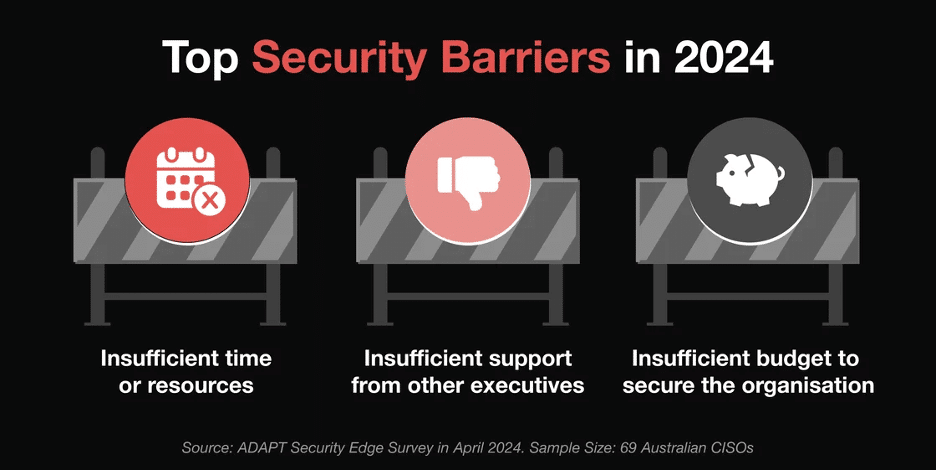
Resource and budget constraints remain considerable challenges, as reported by over 250 Australian CISOs and Heads of Security.
These challenges include budget allocation constraints, excessive manual processes, lack of in-house security skills, and the rapid evolution of security threats.
Stricter government regulations and substantial fines for data breaches further complicate the landscape.
Regulatory pressures necessitate fortified cyber security measures to maintain customer trust and operational integrity.
ADAPT’s April 2024 Security Edge Insights highlighted the need for advanced encryption and secure data handling practices to ensure compliance with new regulations.
Fines of up to $50 million for data breaches highlight the need for compliance and robust security frameworks.
CISOs must navigate these regulatory demands while ensuring their organisations remain resilient against an ever-evolving threat landscape.
Proactive executive engagement, continuous education, and leveraging advanced technologies are vital strategies for strengthening Australian organisations’ cyber resilience.
The next section will delve into these strategic approaches, providing a roadmap for CISOs and tech vendors to effectively navigate the complex cyber security landscape.
Implementing strategic solutions for Australian CISOs
Engaging Executives to Drive Cyber Security Initiatives
Australian CISOs are enhancing executive engagement to tackle cyber security challenges effectively.
According to ADAPT’s Security Edge survey, 58% of organisations stress the need for executive involvement in cyber security initiatives.
CISOs are establishing regular communication channels with executives, providing clear and concise updates on the organisation’s security posture and the impact of current threats.
By involving executives in cyber security exercises and training sessions, CISOs foster a deeper understanding and commitment to the organisation’s security strategies.
Automating security operations for efficiency
CISOs are leveraging automation and advanced technologies to greatly reduce manual workloads and improve the efficiency and effectiveness of their cyber security operations.
According to ADAPT’s research, rolling out automation technologies is a top priority for digital leaders.
Automation tools for threat detection, incident response, and compliance management are key in this process.
By integrating AI and machine learning, CISOs are enhancing their threat detection capabilities, enabling faster and more accurate identification of threats.
Elevating security awareness through continuous education
Continuous education and training are not just important, they are critical components of a robust security culture.
ADAPT’s Security Edge survey highlights that 74% of respondents believe ongoing education for executives is crucial for sustaining support for cyber security initiatives.
CISOs are implementing comprehensive training programs that cover a wide range of topics, from basic cyber hygiene to advanced threat detection and response techniques.
Regular training sessions and workshops keep security teams updated on the latest threats and best practices.
Investing in certification programs and professional development opportunities further enhances the organisation’s security capabilities.
Enhancing incident response capabilities
Developing and maintaining robust incident response plans is vital for minimising the impact of security breaches.
According to ADAPT’s research, 62% of organisations have implemented proactive security measures, including incident response plans and breach readiness assessments.
CISOs ensure that their incident response plans are comprehensive and regularly updated to reflect the evolving threat landscape.
Conducting regular drills and simulations helps security teams practice their response procedures and identify areas for improvement.
Involving key stakeholders in these exercises enhances coordination and communication during an incident.
Australian CISOs build more resilient and secure organisations by focusing on these strategic areas.
Actionable strategies for tech vendors to support Australian CISOs
Provide comprehensive security solutions
Australian CISOs prioritise building secure and trusted organisations, so focus on solutions that integrate seamlessly with existing systems and emphasise early security integration in tech projects.
Demonstrate features such as threat detection, incident response, and data protection to enhance an organisation’s security posture.
Clarify the importance of good DevSecOps practices.
Discuss how incorporating security into the development process can impact market delivery speed and establish your stance.
Share success stories where your solutions prevented breaches and maintained operational integrity to demonstrate their value.
Introduce automation tools for process improvement
Digital leaders prioritise automation to improve processes and operations.
Offer user-friendly automation tools with strong support, focusing on threat monitoring, compliance, and routine security tasks.
Automating these tasks allows security teams to focus on strategic initiatives, increasing efficiency and accuracy while helping CISOs achieve operational efficiency.
Mitigate cloud misconfiguration issues by providing clients with case studies and insights.
Offer training and visibility tools to help them secure their cloud environments and understand potential risks.
Highlight outcomes, not products
Talk about their business outcomes, such as building trust, protecting brand integrity, and enabling business resilience.
Present case studies demonstrating how your solutions have minimised downtime, protected against incidents, and maintained customer trust.
This approach positions your offerings as strategic enablers of business success, making them more appealing to CISOs.
Demonstrate the cost of inaction
Use case studies and reliable insights to illustrate the potential risks and financial impact of not investing in cyber security.
Highlight how cyber crime costs the Australian economy billions annually, and businesses spend hundreds of thousands on cyber security solutions.
Provide examples of how a lack of investment has led to breaches and financial losses, while showcasing how similar companies avoided these pitfalls by implementing your solutions.
Collaborate closely with the CISO’s security team
Position your organisation as a strategic partner that collaborates closely with the CISO’s internal security team.
Offer regular engagements and support, such as regular check-ins with dedicated account managers and technical experts, to help align your solutions with their security goals.
Share case studies where close collaboration led to successful security outcomes, demonstrating your company’s value as a reliable partner that enhances the CISO’s security efforts through consistent and strategic collaboration.
Help CISOs simplify their tech stack by offering integrated solutions that reduce complexity and avoid tool sprawl.
Highlight how your solutions can work cohesively within a larger ecosystem to address their concerns about overlapping functionalities and integration issues.
Provide expertise in Certification Integration
Offer consulting services to help organisations integrate and maintain critical certifications such as ISO 27001, NIST CSF, and PCI DSS.
Share case studies highlighting how your services have helped other organisations achieve and maintain certifications and offer workshops on best practices for integrating these standards.
This positions your company as a trusted advisor with expertise in industry standards, making your solutions more attractive to organisations seeking certification support.
Supporting Australian CISOs requires tech vendors to understand and align with their specific challenges and strategic priorities.
By providing comprehensive security solutions, leveraging automation, focusing on business outcomes, and tailoring offerings to industry needs, vendors can play a crucial role in enhancing the cyber resilience of Australian organisations.