Bolstering Australia’s Cyber Security with Executive Alignment and Strategic Resource Management
Explore how Australia enhances cyber security with executive strategies, expert insights, and innovative solutions to combat rising threats.
Australian CISOs are currently facing a tricky balancing act, dealing with stringent compliance demands while grappling with resource limitations.
This scenario pushes them to realign cyber security strategies more closely with broader organisational goals and compliance frameworks.
Key insights from recent industry discussions point to the critical role of transparent metrics and increased executive participation in cyber security.
ADAPT delves into how these leaders adjust their strategies to manage cyber security governance better and effectively mitigate risks amidst these pressures.
1. Australian CISOs Overcome Cyber Security Resource Shortages and Compliance Challenges
Recent findings by ADAPT reveal that 66% of the nation’s CISOs need more resources, which hampers their ability to manage cyber threats effectively.
Matt Boon, ADAPT’s Senior Director of Strategic Research, highlights the critical need for adequate cyber security budgets to address these deficiencies.

Increase Executive Involvement and Education
Many of Australia’s top security leaders’ focus has shifted towards governance and compliance, driven by increased regulations. This shift detracts from their capacity to concentrate on threat protection and response.
ADAPT’s Security Edge conference spotlighted the crucial matter of executives being more active in cyber security efforts.
Maryam Bechtel, CISO at AGL, advocated for a shift from technology-driven approaches to strategies that align cyber security with overall business goals, calling for executive involvement and shared responsibility in risk management.
Anna Aquilina, CISO at the University of Technology Sydney, suggested continuous education for executives on the evolving threat landscape to bolster cyber initiatives.
Develop Meaningful Metrics and Governance
Panel discussions at the conference accentuated the role of meaningful metrics in assessing cyber security strategies, focusing on making these metrics understandable to non-technical stakeholders to improve organisational transparency.
Tony Vizza, Executive Director of Cyber Security at KordaMentha, highlighted the parallels between corporate and cyber security governance, noting the need for clear roles and proactive management to mitigate risks effectively.

Explore Technological Frontiers and Address Talent Gap
Exploring the technological horizon, discussions addressed new technological frontiers and the implications of AI and quantum computing.
Panellists, including former Jetstar CIO and CISO Claudine Ogilvie and Yvette Lejins, spoke on the role of AI readiness and the disruptive potential of quantum computing against current cryptographic systems.

The talent gap in quantum computing was highlighted with a call for targeted educational and professional training programs to prepare for future challenges.
Key Takeaway: Resource enhancement and strategic executive engagement are crucial for Australian CISOs to manage growing compliance demands and cyber threats effectively.
2. Executive Involvement Shapes Cyber Security Policy and Practices in Australia
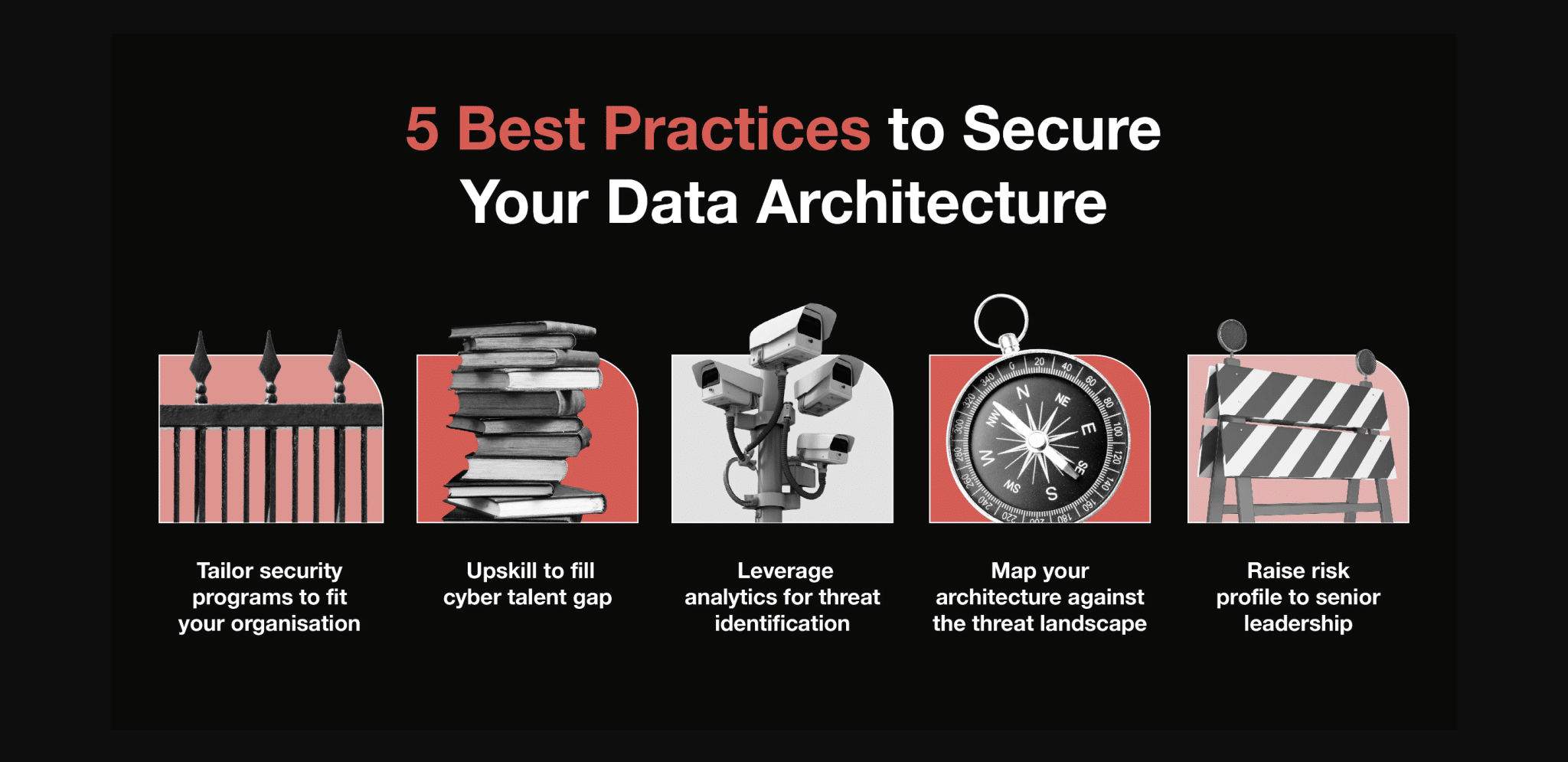
Australian organisations face notable cyber security challenges, as revealed by ADAPT’s comprehensive analysis.
ADAPT’s survey of 158 CISOs showed a troubling lack of engagement at all organisational levels — alarmingly, fewer than half regularly update their leadership on security issues, and only about 50% actively discuss threat mitigation with their teams.
These findings highlight the urgent need for a shift in how security is perceived and managed within organisations.
CISOs must elevate the role of security within their strategic business frameworks to build trust and resilience.
Jamil Farshchi, CTO and CISO at Equifax, further stresses this point, highlighting the essence of transparency and collaboration in Equifax’s post-breach recovery efforts.

By openly communicating about security improvements and engaging with industry peers, Equifax aimed to rebuild trust and enhance their cyber security posture.
This approach aided their recovery and contributed to broader industry improvements.
Address Organisational Gaps with a Multifaceted Approach
In addressing these organisational gaps, ADAPT suggests a multifaceted approach focusing on immediate and strategic actions.
Upskilling current staff, enhancing cyber awareness across the enterprise, and creating career pathways through educational partnerships are essential steps.
Furthermore, implementing ADAPT’s CIAD Model aims to embed security from the outset in data architecture, enhancing threat identification and defence through analytics and fostering a culture aligned with security-by-design principles.
Key Takeaway: Strengthen engagement and skill sets to fortify cyber resilience in Australian enterprises.
3. Behavioural Changes Enhance Cyber Security Resilience in Australian Enterprises
The latest data from the Australian Cyber Security Centre (ACSC) indicates a 13% increase in cyber crime incidents, reaching 76,000 cases last year.
This sharp rise in cyber threats highlights the critical need for Australian organisations to enhance their cyber defences.
Strengthen Organisational Culture and Strategies
The cyber security community’s response is robust. The 2023 ADAPT Security Edge conferences brought together Australian CISOs to tackle these challenges, with discussions from 27 experts across 18 keynotes and panels.

These talks focused on developing resilient organisational cultures capable of managing crises and the complexities of a distributed workforce.
Unified cyber defence strategies and Zero Trust security principles were central themes, reflecting the necessity as breaches occur weekly in one in four Australian organisations.
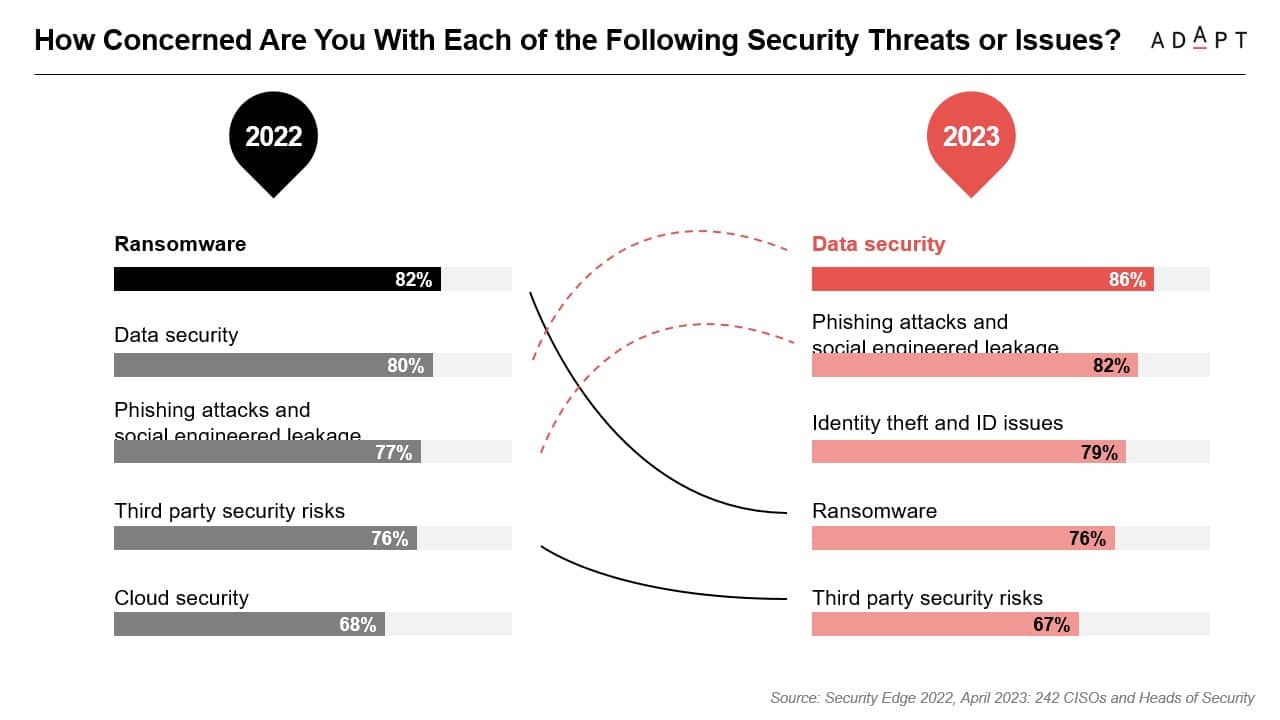
Although 62% of CISOs feel their organisations are prepared, data security remains a top concern, with 86% worried about threats, closely followed by risks from phishing and social engineering at 82%.
Address Broader Challenges with a Multifaceted Approach
Addressing broader challenges requires a multifaceted approach, as technical and budgetary constraints add to the difficulties.
Legacy systems, complex technology stacks, inadequate data ownership policies, budget limits, and manual processes present substantial hurdles.
Insights from a survey of over 250 Australian CISOs and Heads of Security point to the need for better resource allocation and skill enhancement to navigate these barriers.
Key Takeaway: Adopt proactive, unified cyber defence strategies to effectively counter and navigate Australia’s increasing cyber threats.
4. Cyber Security Analysts Develop Effective Strategies Against Escalating Threats in Australia
During the 2023 ADAPT Security Edge event, over 1,000 Australian executive leaders from sectors that comprise nearly a quarter of Australia’s GDP gathered to share insights on enhancing cyber resilience.
Their discussions focused on crisis preparation, risk management, and building a resilient culture, especially within distributed workforces.
Focus on Resilience and Proactive Measures
The discussions underline the ongoing security efforts, revealing that breaches, which used to occur quarterly, now happen weekly for one in four Australian businesses.
In response, CISOs focus on building secure and trusted organisations, enhancing resilience against operational and market-based risks, and boosting operational effectiveness for the next 12 months.
Highlighting proactive security measures, survey data from 242 CISOs and Heads of Security show data security as their primary concern, with 86% reporting it as a noteworthy issue.
Worries over phishing and social engineering attacks follow at 82%.
Address Business and Technical Challenges
These concerns are compounded by business challenges like budget constraints, a need for in-house security skills, and technical issues such as legacy systems and complex technology stacks.
Highlighting the human element in cyber security, 89% of Australian CISOs and Security Heads identify multifactor authentication tools as the most effective technology for combating cyber threats.
Kevin Mitnick, a world-famous hacker, and top cyber security speaker points out the critical role of addressing human factors in cyber security, stating, “Companies spend millions on firewalls and secure access devices, and it’s money wasted if it doesn’t address the weakest link: the people.”
Advocate for Advanced Security Models
The ADAPT discussions consolidated the security efforts and accentuated the imperative of a unified approach to cyber security.
Cyber security experts Kylie Watson, Alan Marjan, and Tom Kenyon stressed the need for collaboration across the workforce to combat threats like ransomware and state-based actors.
They noted that proper training in security best practices and investment in robust security technologies are beneficial and essential.

The event advocated for the adoption of advanced security models, including Zero-Trust security models, which involve continuous verification of all entities on a network.
These models effectively minimise risks and reduce the attack surface.
Key Takeaway: Australian enterprises are advancing their cyber security strategies, integrating comprehensive measures to tackle an escalating array of cyber threats effectively.
Conclusion
Australian CISOs are navigating stringent compliance demands and resource shortages by realigning cyber security priorities with broader organisational goals.
Enhanced executive engagement and developing transparent, understandable metrics are crucial for effective cyber security governance.
The analysis of recent industry discussions shows that these strategic adjustments are part of a broader, proactive approach to integrating cyber security into the organisational fabric.
These efforts aim to mitigate current threats and prepare for future challenges, strengthening resilience against an increasingly sophisticated cyber threat landscape.
These strategic adaptations are essential in the ongoing effort to safeguard Australian organisations.

























