5 Best Practices to Secure Your Data Architecture
ADAPT's recent reports highlight critical challenges in cyber security, including increased workload and fatigue among security teams, along with a notable shortage of in-house security skills.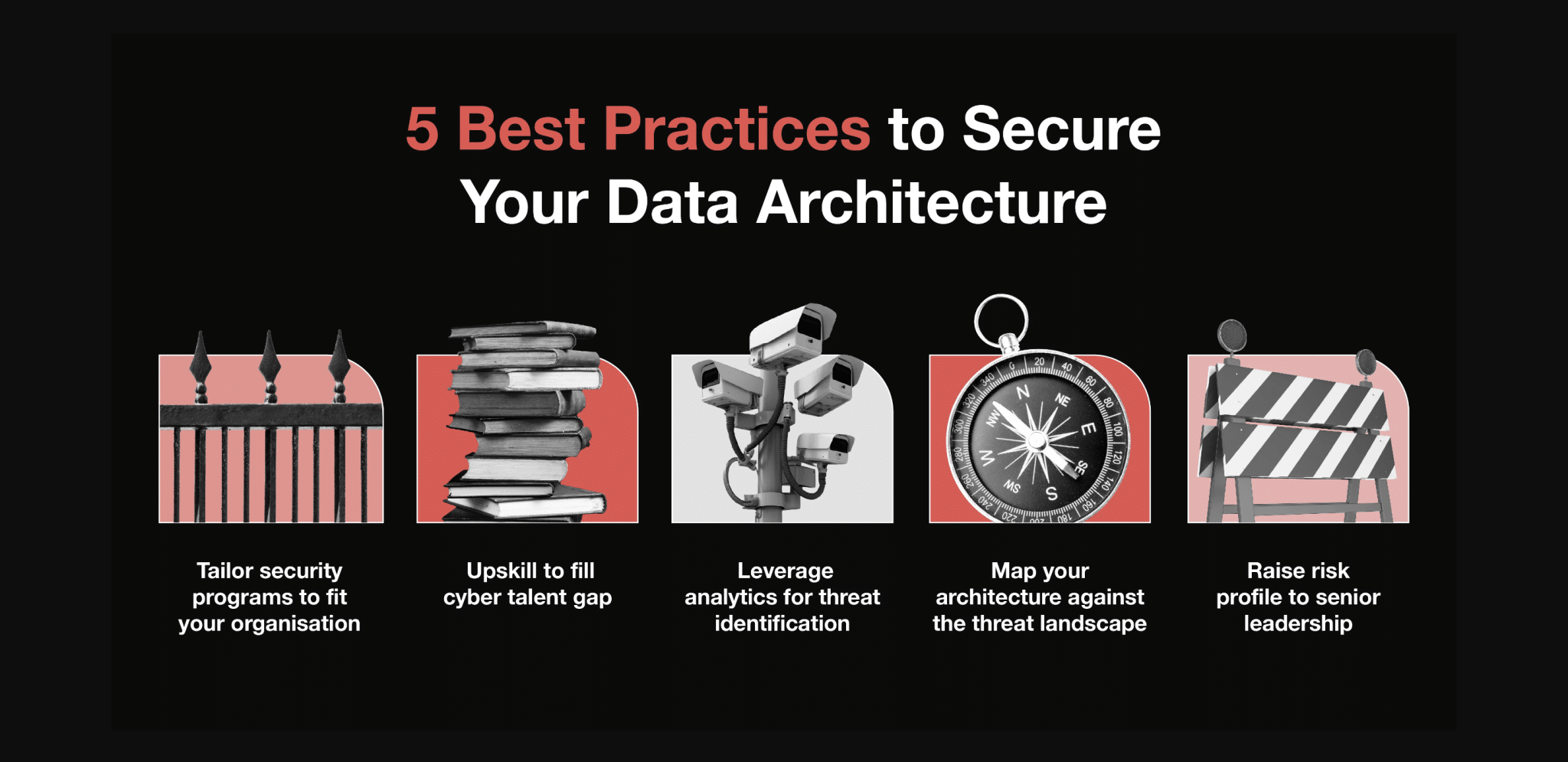
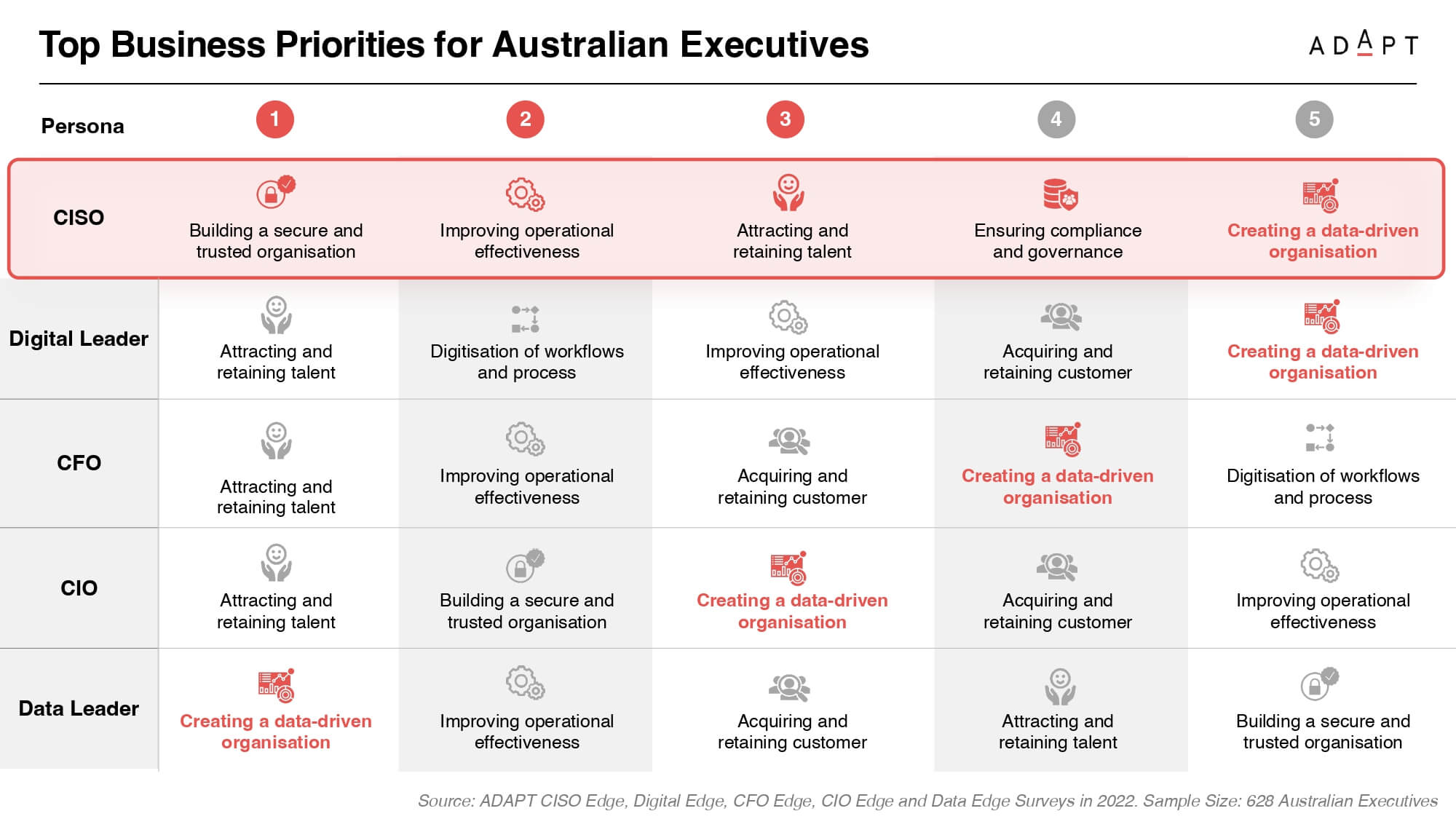
For Australian Chief Information Security Officers (CISOs), the next 12 months are all about bolstering trust within their organisations.
This strategic focus extends to the second position for Chief Information Officers (CIOs) and claims the fifth spot for Chief Data Officers (CDOs).
ADAPT’s Research and Advisory clients can access the full report, Five Actions to Connect, Resource and Secure a Resilient Data Architecture.
To align security initiatives with the demands of creating a secure and trusted organisation, ADAPT recommends embracing these five essential pillars:
Best Practice 1
Fortify Organisational Resilience: Take Immediate Action on Alarming Gaps in Cyber Security Engagement Revealed by ADAPT Survey
ADAPT’s survey of 158 CISOs has uncovered a concerning trend: a widespread lack of engagement in cyber security across all organisational levels.
Alarmingly, fewer than half of these CISOs regularly update their executive leadership and the Board on security matters, and only about 50% engage with their teams to discuss threat mitigation roles.
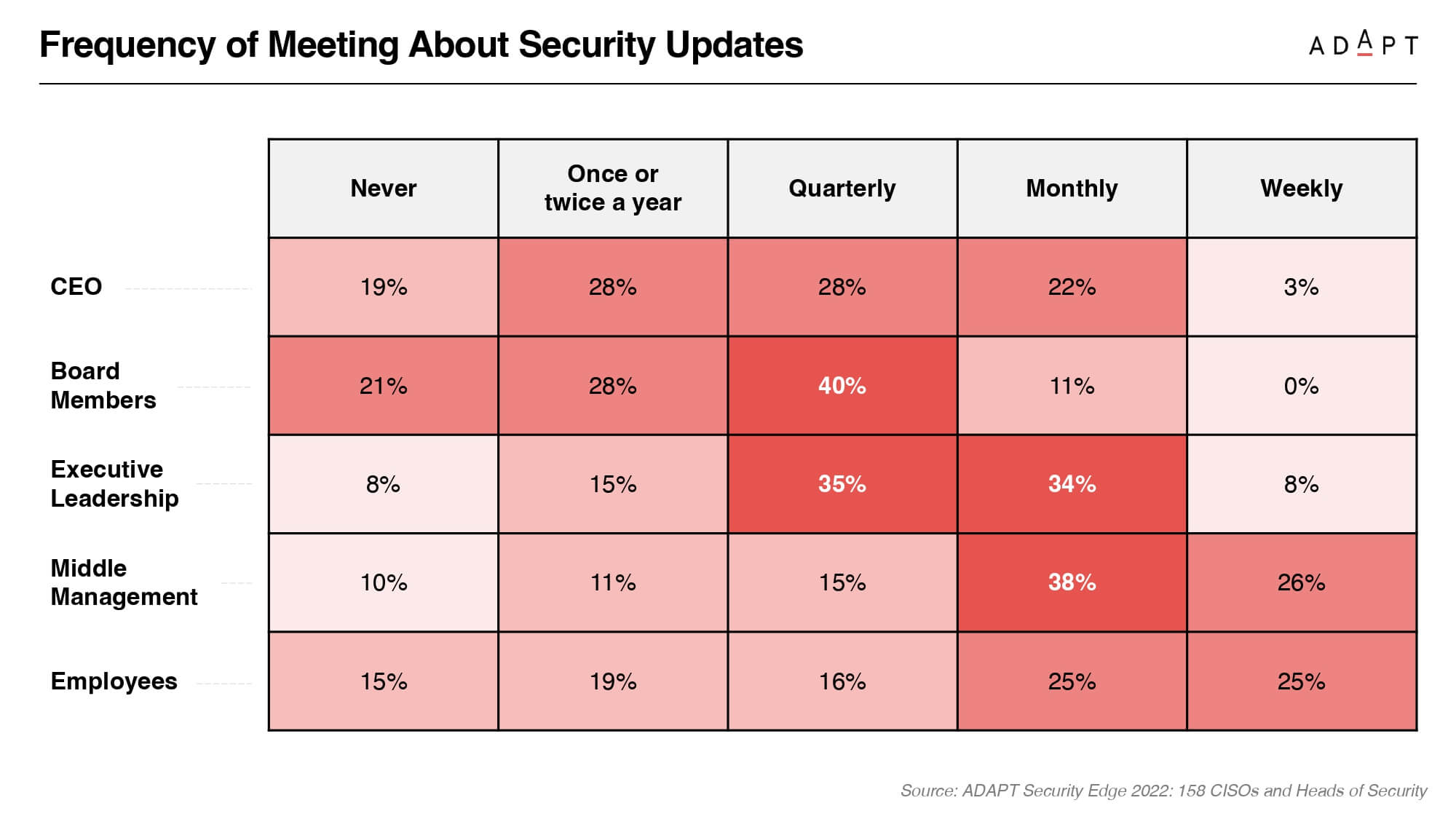
It’s clear that CISOs need to step up their game in communicating the cyber security landscape and its role in protecting business value, especially at higher organisational echelons.
For CISOs, this means:
- Tailoring security programs to fit your organisation.
- Identifying and empowering change advocates in your teams.
- Highlighting how all individual’s actions impact the organisation’s security.
Together, these steps create a strong case for IT investment, propel cyber security programs’ success, and foster a culture shift among employees towards greater security and resilience.
Key Action Steps:
Address critical gaps urgently by:
- Focusing on business value.
- Aligning security initiatives with the organisation’s vision.
- Developing a common language with executives.
- Implementing tailored security programs.
- Finding change champions within teams.
- Emphasising individual behaviors.
These actions build a compelling case for IT investment, ensure cyber security program success, and drive meaningful behavioural change—strengthening organisational security and resilience.
Best Practice 2
Tackle Cyber Security Challenges: CISOs Take Action to Combat Workload Surge, Address Talent Shortage, and Strengthen Security
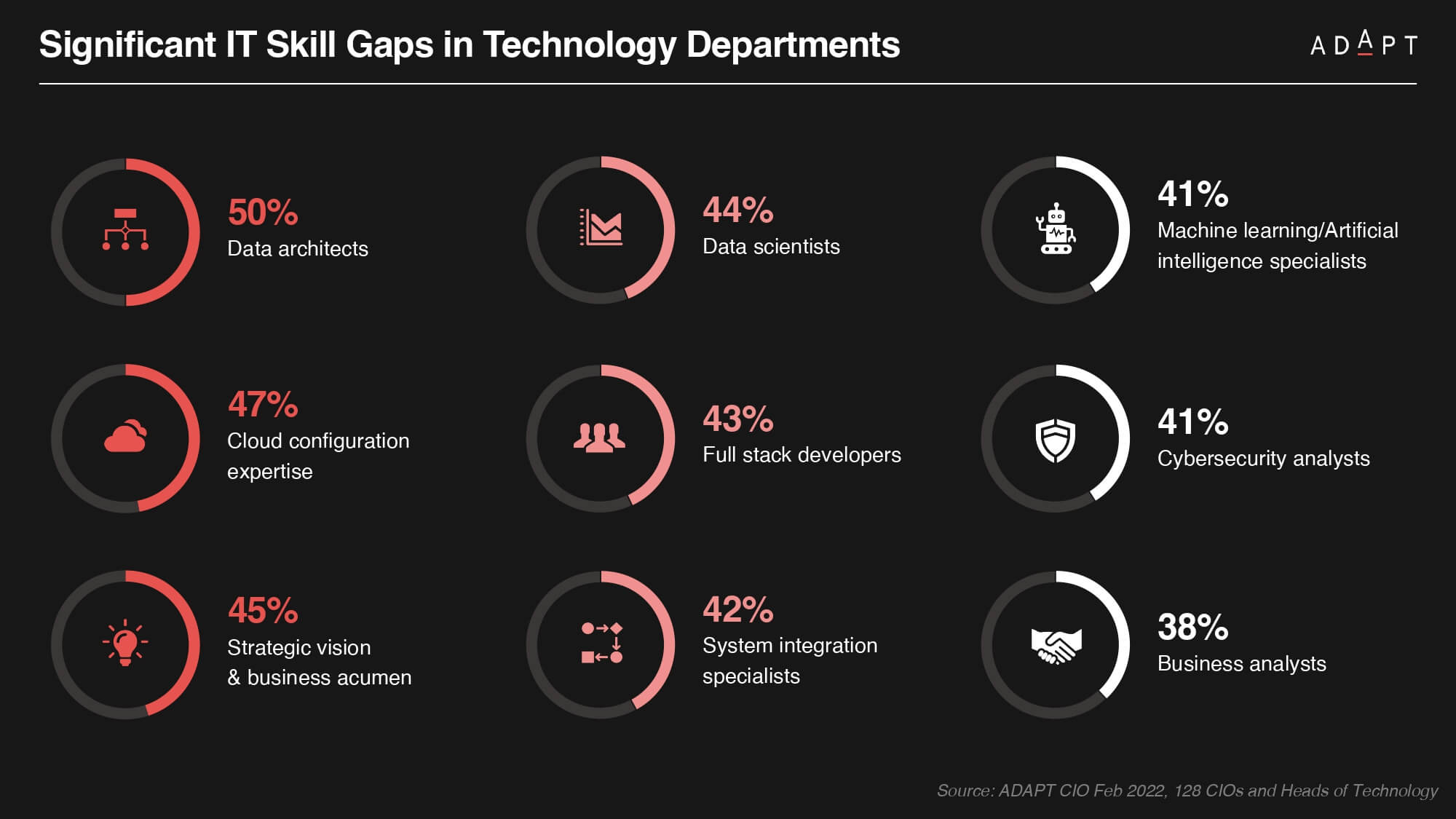
ADAPT’s recent reports highlight critical challenges in cyber security, including increased workload and fatigue among security teams, along with a notable shortage of in-house security skills.
These challenges resonate with Australian CIOs, who grapple with the need for more business acumen, stronger cyber security awareness, and skills to manage complex, hybrid cloud systems and data architectures.
To proactively bridge these talent gaps, CISOs are urged to:
- Upskill existing staff.
- Work with Chief Human Resources Officers to incorporate cyber awareness into learning programs.
- Form partnerships with educational institutions to create career pathways.
- Focus on diversity and inclusion initiatives.
These foundational actions are instrumental in alleviating workload and enhancing risk management but also align with Equifax CISO Jamil Farshchi’s advice on keeping a balanced talent mix that can effectively combat business breaches.
Key Action Steps:
To recap on tackling cyber security challenges effectively:
- Upskill Your Staff: Proactively train your team to enhance in-house security skills.
- Collaborate with CHROs for Cyber Awareness: Integrate cyber awareness into learning programmes, emphasising analytical, data, and behavioural competencies.
- Forge Educational Partnerships: Work with tertiary institutions to establish career pipelines, focusing on critical thinking and cultural change.
- Prioritise Diversity and Inclusion: Implement initiatives to diversify your workforce, creating a mix of experiences and backgrounds for proactive problem-solving.
These actions enable CISOs to close talent gaps, reduce workload, improve risk management, and strengthen organisational cyber security resilience.
Best Practice 3
Forge a Cyber-Resilient Data-Driven Future: Key Steps for Immediate Action from ADAPT’s 2022 Research
ADAPT’s 2022 research, involving 638 Australian business executives, highlights a collective commitment among CIOs, CDOs, CFOs, and Data Leaders towards constructing a data-driven organisation, with CISOs ranking it as their fifth business priority.
This focus aligns with the understanding that Australian organisations managing significant data volumes can gain significant business value by securing and safeguarding this data.
The focus extends to enhancing decision-making, keeping customer trust, and optimising operational effectiveness.
Integrating security principles into data-driven architectures offers three key advantages:
- Enhanced threat identification and defence through analytics
- Informed decision-making leading to competitive edge and
- A foundation for a security-by-design culture
CISOs should apply ADAPT’s CIAD Model to realise these benefits and create a secure data architecture.
They are also encouraged to educate technology teams, executives, and business users on practices that reduce the risk of confidential data leaks.
This comprehensive approach aims to build a culture of cyber security readiness, ultimately strengthening the organisation’s data-driven strategy.
Key Action Steps:
To effectively address cyber security challenges:
- Apply CIAD Model: Design a secure data architecture prioritising security in data collection, integration, and analysis.
- Empower Data Experts: Equip data scientists and machine learning experts for enhanced incident detection, prevention, and response.
- Educate on Secure Behaviors: Instruct technology teams, executives, and users on behaviours mitigating the risks of confidential information leakage.
These actions fortify the organisation’s data-driven strategy, ensuring enhanced security, informed decision-making, and a resilient, culture-aligned approach to data management.
Best Practice 4
CISOs Build Resilience: ADAPT Market Trends Insights
The ADAPT Market Trends report indicates that the improvement in threat management reported by 85% of Australian organisations by April 2022 is mainly due to a few top performers. There’s a need for more comprehensive planning and design and a risk of burnout among skilled security personnel.
Simultaneously, a survey of 160 CISOs pinpoints top concerns, including ransomware, data security, phishing, third-party risks, and cloud security, highlighting these threats’ centrality to data, people, and technology architecture.
CISOs are advised to map the organisation’s architecture against the threat landscape, assess specific vulnerability portfolios, and measure outcomes related to process hardening and security awareness.
Additionally, evaluating cyber intelligence coverage, toolchain integration, and incident detection efficacy is crucial.
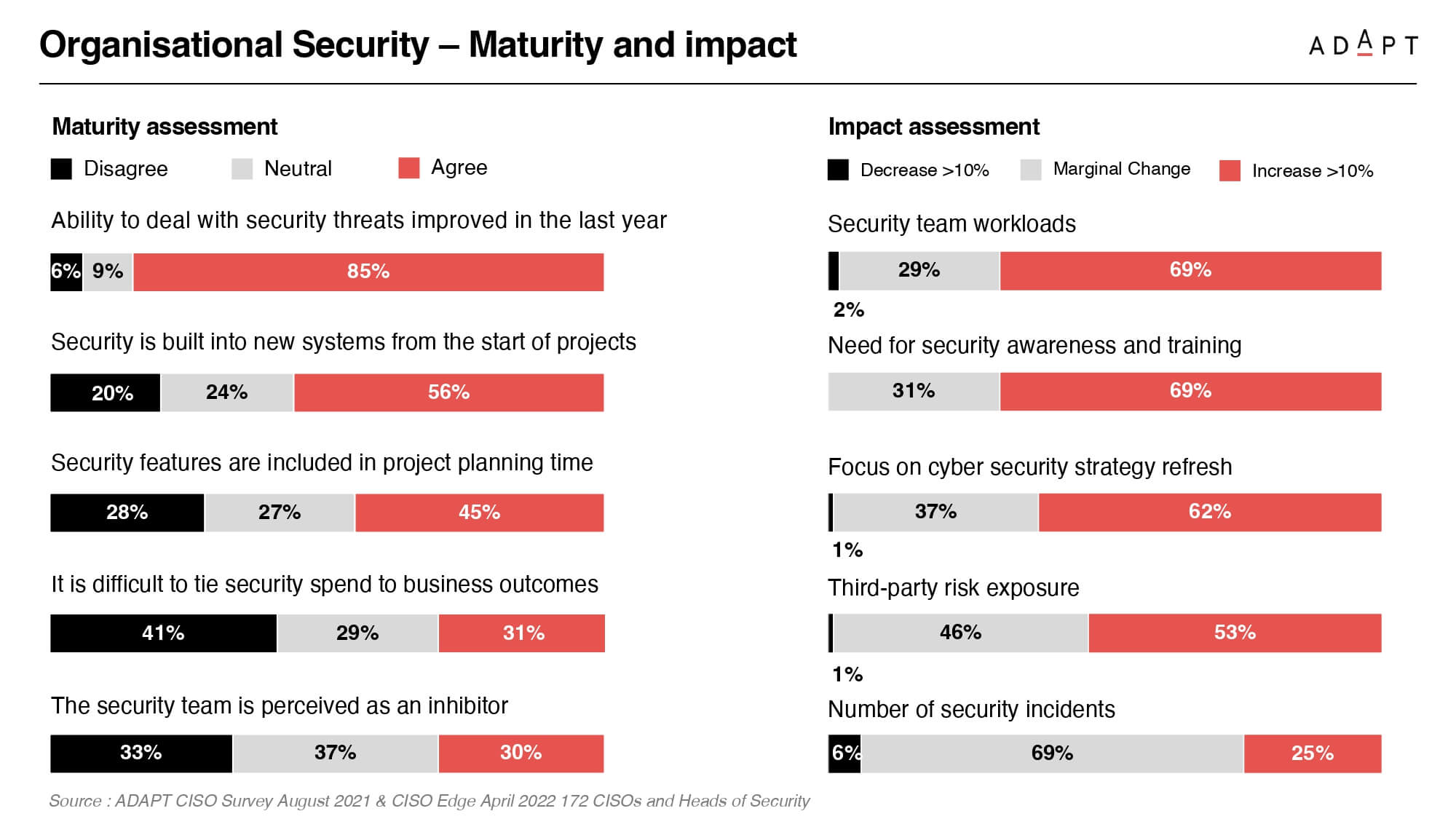
The report recommends shortlisting effective technologies such as multi-factor authentication, endpoint security, and SIEM based on the vulnerability portfolio to create a prioritised roadmap.
By developing an adaptive defence framework aligned with organisational policy and external regulations, CISOs can prioritise investments to minimise risks.
This approach, highlighted by Ansvar IT Manager Heather Santin in an ADAPT Market Trends report from April 2022, emphasises engagement over mere compliance.
Key Steps:
- Map Architecture: Find vulnerabilities by thoroughly mapping the organisation’s architecture against the threat landscape.
- Assess Portfolios: Evaluate vulnerability portfolios, measuring process hardening, security awareness, and business maturity.
- Evaluate Intelligence: Assess cyber intelligence coverage, toolchain integration, and incident detection efficacy.
- Shortlist Technologies: Prioritise effective technologies like multi-factor authentication, endpoint security, and SIEM based on vulnerability portfolios.
- Develop an adaptive framework: Align with organisational policy and external regulations, prioritise investments for risk minimisation, and emphasise engagement over compliance, as suggested by Heather Santin in an ADAPT Market Trends report from April 2022.
Best Practice 5
Act Now for Cyber Resilience: Ensure Seamless Security Interoperability and Posture Maturation
Organisations face challenges in ensuring the seamless interoperability of people, processes, and technology with security at the forefront.
The ADAPT Persona Mapping report reveals a concerning statistic — only 45% of organisations incorporate security planning at the start of their IT initiatives.
Additionally, 33% need help with suboptimal security tooling, compounding the workload for CISOs and their staff as they navigate a complex threat landscape.
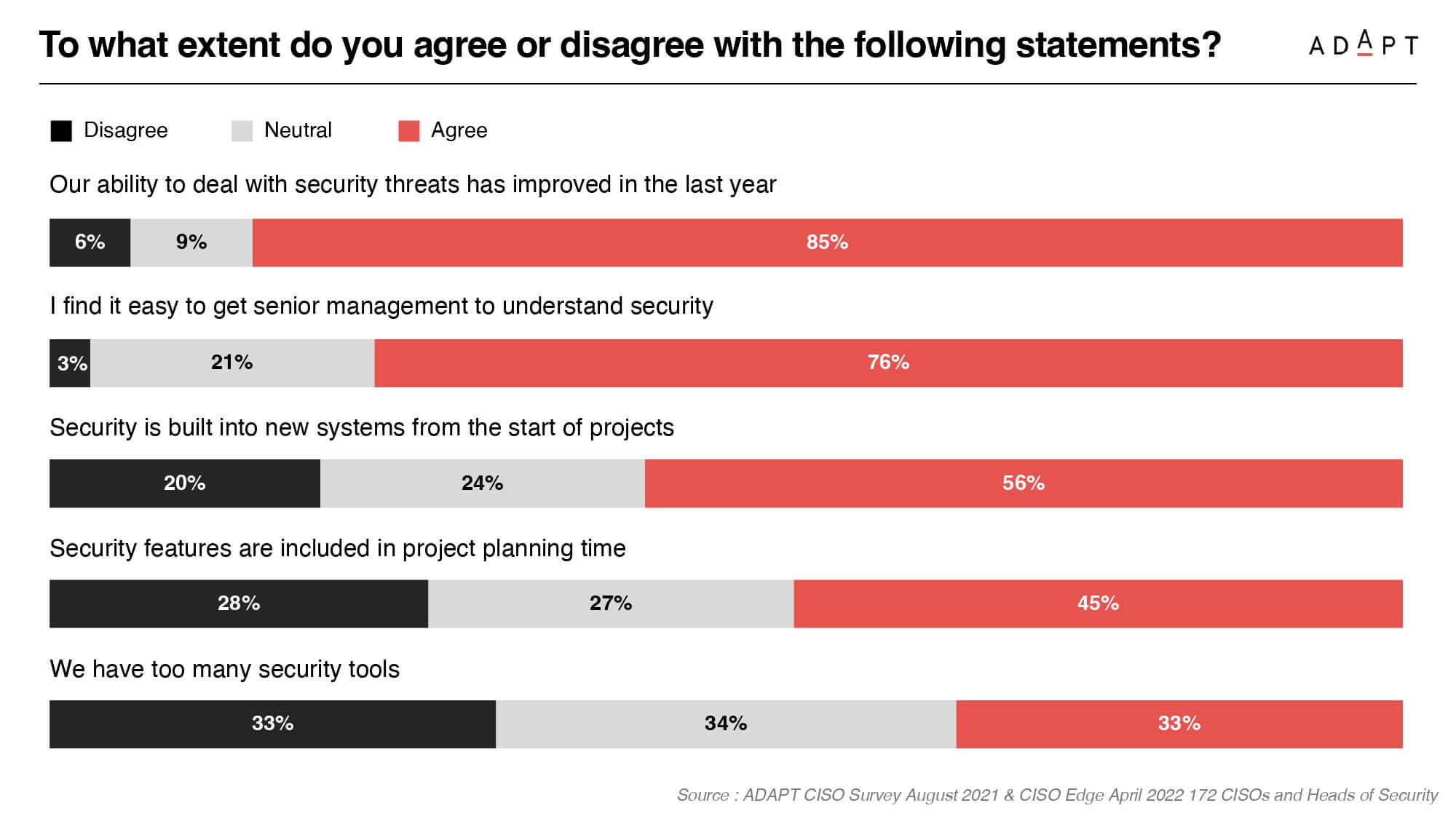
The repercussions of inadequate interoperability become clear as threat monitoring data generated by these systems often stays invisible to business users, complicating the assessment and prioritisation of changes.
To address these issues, recommended actions include:
- Communicating the genuine risks associated with interoperability issues to senior leadership.
- Advocating for the strategic integration of security into planning and design.
- Enhancing vendor evaluation frameworks to prioritise security outcomes.
These actions aim to revolutionise the approach to acquiring and consuming security IT, fostering a mature cyber posture within the organisation.

Chief Security Officer Andrew Webster from Transgrid underscores the significance of being safe and secure by design in all decision-making processes, highlighting the pivotal role of architectural design in maturing the organisation’s cyber posture.
Key Action Steps:
- Communicate real risks of interoperability to leadership.
- Advocate for strategic security integration in planning.
- Enhance vendor evaluations by prioritising security outcomes.
Conclusion
CISOs must ramp up engagement, bridge talent gaps, and strengthen data-driven strategies that align with organisational goals tackle urgent cyber security challenges effectively, as highlighted by ADAPT’s research.
Implementing key actions fosters resilience and ensures organisations confidently navigate the digital landscape.
ADAPT’s Research and Advisory clients can access the full report, Five Actions to Connect, Resource and Secure a Resilient Data Architecture.
























