Security leaders are stretched thin and expected to deliver more with less.
Across Australia’s enterprise and midmarket, CISOs are managing transformation pressure, GenAI risks, and mounting board scrutiny, all while foundational gaps persist.

ADAPT’s 2025 State of Cyber Security report makes one thing clear.
The foundations are still weak. Most security teams remain under-resourced, over-stretched, and stuck operating in reactive mode.
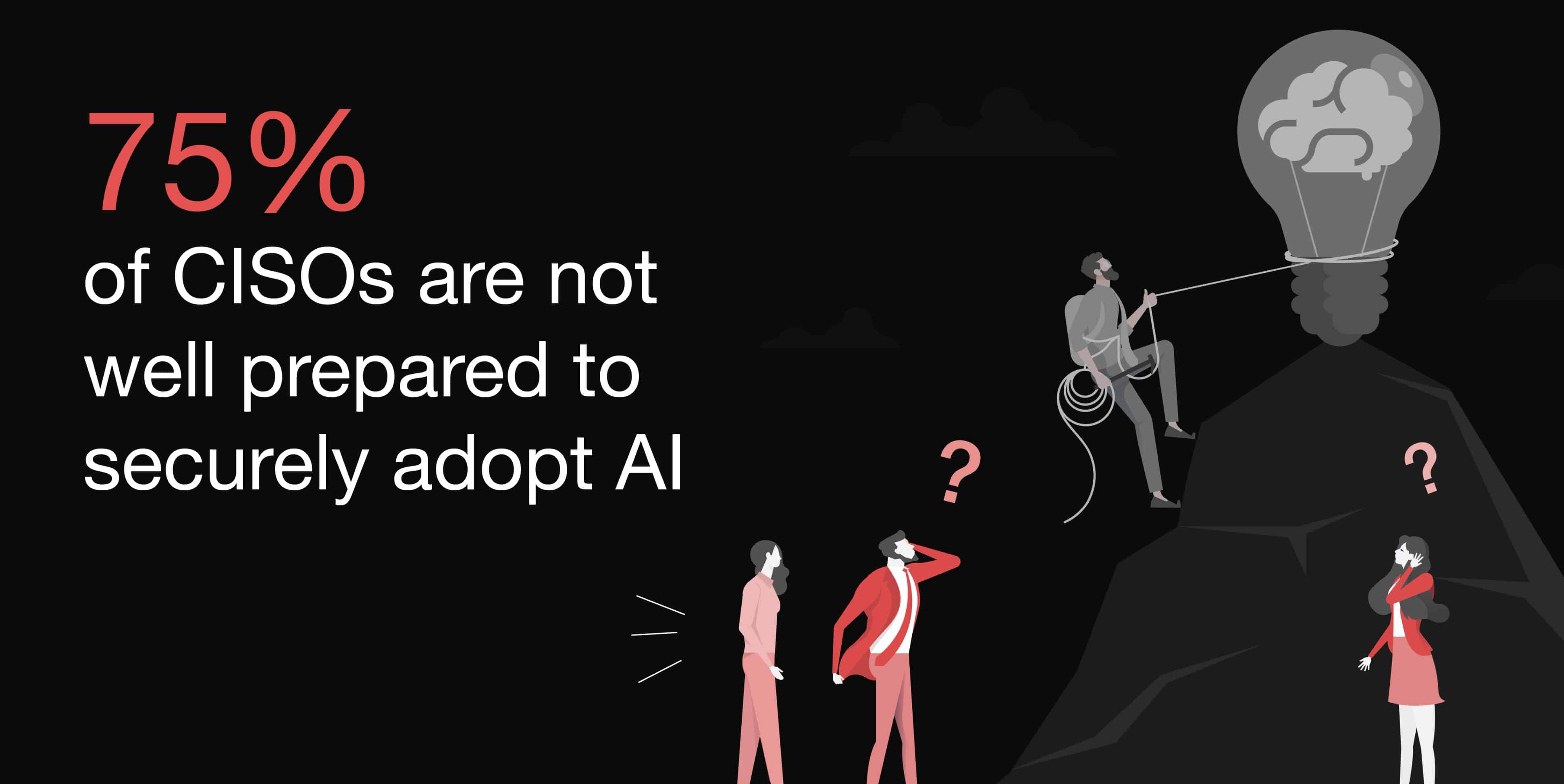
The execution gap on the Essential Eight persists, AI governance is patchy, and few CISOs are reshaping the language of security to align with business priorities.
To explore what this means on the ground, ADAPT Senior Research Analyst Pooja Singh sat down with Content Marketing Manager Justina Uy to untangle the real challenges holding security leaders back, and how to shift from compliance mode to embedded resilience.
Essential Eight success starts with fewer priorities and more self-awareness
Many CISOs are trying to cover too much ground with too few resources.
The foundational problem is often strategic overload. Small and midsized organisations in particular are burning time spreading effort across all eight controls instead of anchoring effort to the most impactful gaps.

Pooja Singh urges security leaders to reduce scope and start with a focused “big three” set of controls.
“Instead of going through all eight, I would say start small with the big three controls. It could be multi-factor authentication, patching, backups.”
From there, the next step is prioritisation based on evidence.
Reviewing audit reports, incident logs, and credential-based attack patterns helps pinpoint which controls deserve deeper focus.
Organisations experiencing a high volume of phishing or credential abuse should lock in MFA.
Environments flooded with unapproved applications should direct effort toward application control.
The execution gap widens when organisations treat Essential Eight as a checklist rather than a tailored path based on threat realities and existing maturity.
GenAI adoption needs clear brakes before acceleration
Security teams are under pressure to support the use of GenAI, but the rush to deliver pilots has far outpaced the deployment of basic safeguards.
ADAPT’s 2025 State of Cyber Security report shows AI-related risk is top of mind, yet few organisations are equipped to address it meaningfully.
Pooja Singh illustrates this risk vividly.
“Think of GenAI as a sports car… if you drive it without brakes, without any road sign, without any seatbelt, there’s a good probability that very early on, you will crash.”
Before deployment, security teams need to map and lock down sensitive data, source code, and internal IP.
Anything exposed through generative tooling must be categorised and protected early.
Governance policies, permissioning, and audit trails are prerequisites for safe experimentation.
The skills gap makes this harder. Few teams have the bandwidth to both learn the tech and govern its use.
But when teams are empowered to adopt GenAI with structured guidance and recognition for innovation, safe adoption scales faster.
The most effective models reward autonomy and align usage with career progression, creating a culture where secure experimentation becomes the norm.
CISOs must reposition SoC capabilities to align with business value
In many organisations, the Security Operations Centre is still positioned as a technical command post focused on alerts and throughput.
That framing limits its perceived value.
According to Pooja, CISOs need to pivot from metrics that show activity to narratives that show impact.
“Instead of saying, ‘Oh, we blocked a thousand attacks,’ you can change the language to ‘We stopped a phishing attack that would have exposed client records or cost this much to the business.’”
This shift is especially important when working with outsourced SoC providers.
Leading CISOs bring those partners into quarterly business reviews to maintain visibility, track mean time to containment, and show how disruption is being actively reduced.
Security teams that translate their technical work into risk outcomes are more likely to secure executive buy-in.
This includes linking response times, containment effectiveness, and threat volumes directly to metrics the board already tracks.
CISOs have the tools; they just need to reframe their use
The biggest takeaway from ADAPT’s cyber security research and frontline interviews is that most security teams are sitting on underused assets.
They already have incident data, vendor access logs, threat models, and risk reports.
What they often lack is a way to activate these tools and communicate their relevance to broader transformation goals.
Pooja Singh summarises the opportunity clearly.
“Look for things which are already in your system and how you can showcase that they impact the delta or the change… you don’t have to reinvent the wheel.”
Instead of waiting for budget cycles or technology upgrades, security leaders should start by amplifying what they already control.
This includes surfacing metrics that reflect business impact, elevating early success stories from internal AI adoption, and creating a culture where experimentation is recognised.
Risk-intelligent organisations build on what already exists, using internal signals to guide better decisions, shift perception, and reduce firefighting.
Recommended actions for cyber security leaders
Security leaders looking to close execution gaps and build stronger alignment in 2025 should take the following steps now:
- Start small and prioritise by threat history. Limit focus to three Essential Eight controls and tailor investment based on recurring incident trends and audit insights.
- Secure GenAI before enabling it. Map and control sensitive data first, then introduce GenAI use cases with policy, training, and audit visibility already in place.
- Shift security language to business impact. Stop reporting on volume and start showcasing how interventions reduce exposure, save costs, and prevent disruption.
- Make SoC performance a shared concern. Invite managed SoC providers into quarterly planning and translate detection into risk metrics business units care about.
- Mine existing tools and reports for proof. Use what is already being tracked internally to frame wins, support funding conversations, and guide capability alignment.
Security leaders do not need to wait for new tools or budget cycles to evolve their posture.
The path to resilience starts with sharper focus, clearer language, and better use of what’s already available.
To benchmark your organisation against national trends and learn how other CISOs are closing Essential Eight gaps, managing GenAI risks, and aligning with business priorities, download ADAPT’s State of Cyber Security 2025 report.