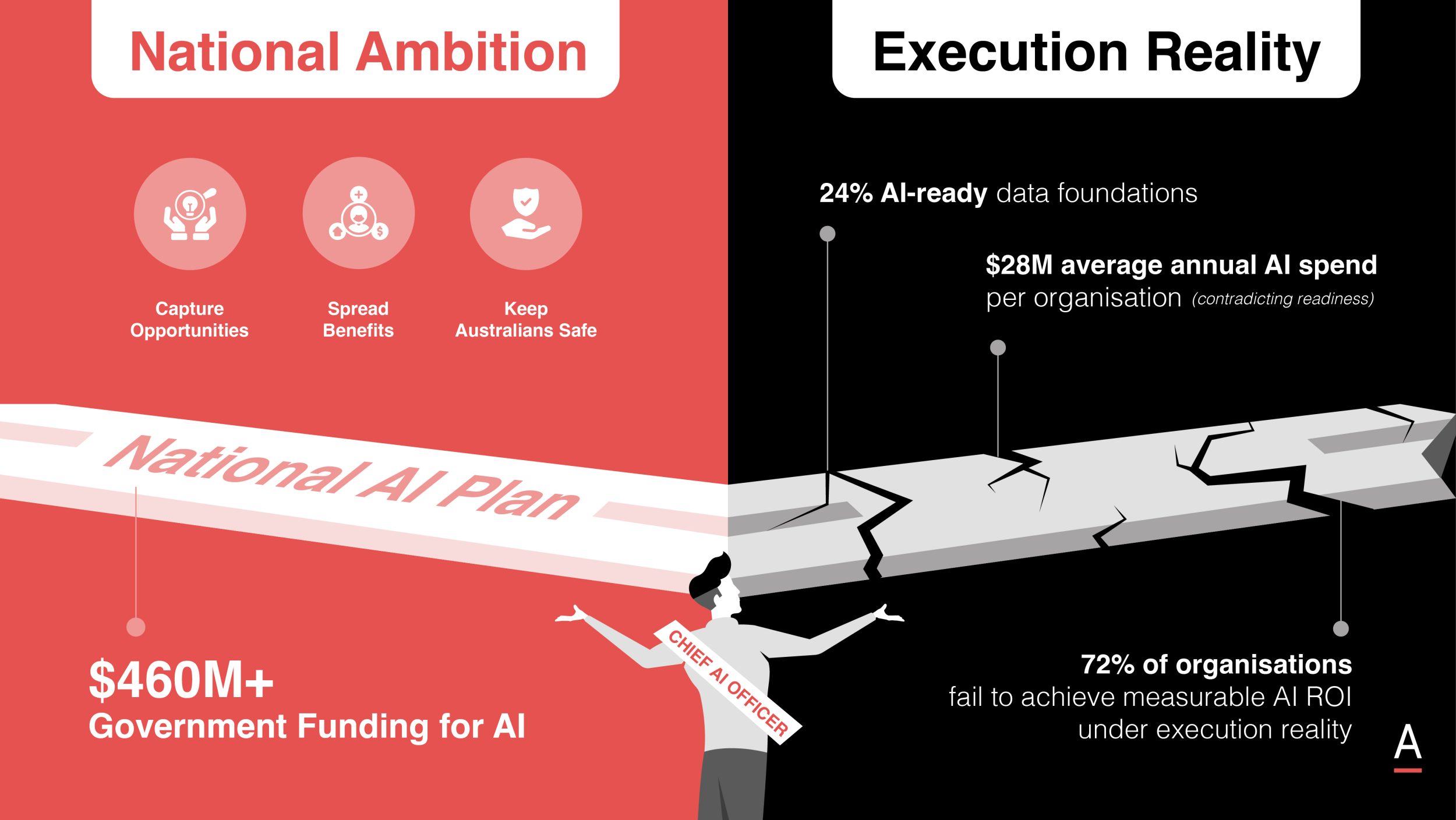
The Principles of Zero Trust Security
The Zero Trust system secures IT network infrastructure end-to-end by implementing the following principles: Continuous User Validation, Minimum Privileges, Device Access Control, Multi-Factor Authentication (MFA), and Visibility and Analytics.
Before the popularity of the Zero Trust security framework, the default security standard was the “castle-and-moat” or perimeter-based system, where most efforts were directed towards making it difficult to gain access from outside the network.
In contrast, everyone inside the network was trusted with access by default.
The inherent flaw of this system is that it does not consider the sophisticated nature of attacks on the network.
Intrusion prevention tools like firewalls may stop some attacks, but a single breach would be catastrophic for the organisation, as the attacker gets free reign over everything inside.
Zero Trust security principles, however, are designed to defend against even the most intelligent attacks.

Defining Zero Trust Security
The philosophy behind Zero Trust security is that trust should not be automatically given to anything inside or outside its perimeters. Instead, anything and everything that tries to connect to its systems must be verified before being granted access.
It works by having all users authenticated, authorised, and continuously validated to be granted access to applications and data, regardless of whether they are from the organisation’s network or outside.
With this more rigid form of security, attacks and breaches have slimmer chances of success and would be more manageable because the organisation is protected from within.
The Zero Trust security model aligns with CISO priorities
When it comes to planning and implementing security initiatives, ADAPT’s 2022 Security Edge survey has revealed that Australian CISOs have listed the following as their most important drivers in security initiatives:
- Ensuring data privacy
- Preventing brand damage
- Preventing data loss
- Customer trust
- Securing end-users
This comes as no surprise, as phishing, malware, ransomware, data theft, and data exfiltration attacks are destructive and familiar, highlighting the importance of Zero Trust security.
They are so prevalent that according to ADAPT’s 2022 Security Edge Survey, 77% of CISOs expected security budgets to increase in 2022 over 2021. Additionally, it is worth noting that 91% of Australian CISOs say “building a secure and trusted organisation” is their number one business priority.
Comparatively, surveyed Australian CIOs say their number one business priority is “Improving operational effectiveness” as their top business priority. At the same time, that is the second priority for CISOs based on the survey.
The 5 principles of Zero Trust security
The Zero Trust system secures IT network infrastructure end-to-end by implementing the following principles:
- Continuous User Validation
Under a Zero Trust security system, it is assumed that attackers may come both from within and outside the network, hence the constant need to verify user identity, device identity, and privileges. A good example is when user logins and connections are timed out periodically, forcing repeated verification on users and devices upon login. - Minimum Privileges
Minimising users’ exposure to sensitive parts of the network is key to minimising the risk of breaches and attacks. This works by giving the users only as much access or information as they need. Cloud-based workloads, containers, and functions are attractive to cybercriminals. Tailored access monitoring and access management are essentials for protecting these assets. - Device Access Control
Under Zero Trust principles, all devices connected to the corporate network are treated as untrusted and potential threats. Continuously monitoring the number of devices that are trying to access the network and verifying the authorisation of each device minimises the chances of breaches on the web. This principle also helps administrators identify devices that are threats and isolate them as needed. - Multi-Factor Authentication (MFA)
Compromised user credentials are the leading cause of data breaches. Authentication via a username and password is no longer enough. MFA protects the network by requiring more than one piece of user evidence for their authentication. A good application of this is the 2-factor authorisation used by online platforms, wherein users need to enter a code sent via SMS on top of their account password, providing two pieces of evidence to prove whom they claim to be. - Visibility and Analytics
Visibility into activities on devices associated with the network is critical in making informed access decisions. These analytics must be monitored, logged, and correlated regularly.
9 Zero Trust security best practices
CISOs note lack of budget allocation as their 6th biggest inhibitor to implementing security initiatives:
- 31% of CISOs say it is challenging to tie security spending to business outcomes
- 16% of CISOs say security expenditure is difficult to justify
- 40% of CISOs say it is challenging to tie security spending to business outcomes.
With these figures from ADAPT’s 2022 Security Edge Survey, it’s essential to be mindful of the Zero Trust security best practices to get your money’s worth.
- Implement consistent security policy across all use cases, users, applications, and infrastructure. This ensures that the same people have access to applications and services in every location, with the same level of authentication, traffic inspection, and access privileges.
- Decrypt traffic to gain visibility over them, which allows easier inspection and prevention of malicious activity.
- Stay on top of your security by constantly validating users, applications and infrastructure. Filter out unknown traffic from your network.
- Only allow the level of access required for each user, service, or API, per the least privilege access principle.
- Choose a platform that integrates all your products into one rather than a collection of point products that don’t work well together.
- Protect all your endpoints, including IoT devices that you do not manage.
- Before architecting your Zero Trust environment, thoroughly review how it can be aligned with your organisation’s goals and desired outcomes.
- Protect your data centre and business by designing your Zero Trust system from the inside out instead of the outside in. Your most valuable assets are more likely to be in your data centre than your perimeter.
- Begin the project by first securing the most critical segments of your business, such as propriety code repositories, customer data, and the like, before gradually transitioning to a Zero Trust environment.
Zero Trust security benefits all
As the old firewalls surrounding the corporate network become obsolete amid the rush to adopt a hybrid workspace, Zero Trust security has become essential to protecting all sectors.