Rethinking Security When Security is Deprioritised
ADAPT data from October and November 2020 shows that although pandemic-induced disruptions heightened organisational focus for security and risk management, prevailing adverse culture, limited skillsets, infrequent training, and limited funding held back efforts to mature cyber resiliency.
Introduction
These last nine months since March 2020 have required technology leaders to spearhead an innovative, technology-led response to a thoroughly unprecedented operating environment. Almost overnight, organisations accelerated digital transformation at a blistering pace and sought to secure assets, information, and people across complex multi-cloud and work from home environments.
As organisations refocus on a pathway to growth, ADAPT advises that IT and business leaders must:
- Realign technology to build the data-driven organisation
- Embrace new ways of innovation to enhance the human experience
- Rethink security to fit a hybrid operating environment
This third and final part of ADAPT’s exploratory series concludes our Nine Paradigms for an Extra-Ordinary World. Here, we will examine one of these three final paradigms: Rethink Security.
We base our examination of these paradigms on our ongoing engagement with IT and business leaders in Australia and New Zealand.
We provide pragmatic advice to enable local organisations to thrive in the next normal that has emerged from the fundamental public health, economic, and social disruptions that have prevailed for the past nine months.
Rethink Security
The rush to remote in 2020 required security leaders to defend an expanded perimeter.
ADAPT data from October and November 2020 shows that although pandemic-induced disruptions heightened organisational focus for security and risk management, prevailing adverse culture, limited skillsets, infrequent training, and limited funding held back efforts to mature cyber resiliency.
CISOs partnering with the CIO to build a secure and trusted organisation should:
- Invest in remaking cybersecurity strategies appropriate to modern hybrid operations
- Allocate time and effort to refactoring awareness programs to suit cross-functional needs
- Implement digital risk assessments to mitigate supply chain vulnerabilities

Remake cybersecurity strategies to enable business resilience
CIOs seeking to build a resilient, cloud-first operating model need to address fundamental strategic and tactical disconnects that require a rethink of how the organisation deploys security.
Architectural hardening is crucial to facilitate hybrid operations. The effort to enable a heterogeneous perimeter requires CISOs to augment frameworks created to defend core systems with access granted to trusted users in dependable locations.
Multi-cloud complexities, work-from-home vulnerabilities, and increasing attack vectors all contribute to the challenge for CISOs to enable business resilience in a zero-trust world.
Yet CIOs and CISOs differ in their approach to securing the organisational fabric. Although 37% of CIOs plan major upgrades for security frameworks and 13% expect to implement a complete overhaul; 75% of CISOs articulate that the race to remote creates an urgent need for attention to the organisation’s defensive fabric.
Businesses are increasing funding across the security dimension. Some 64% of CIOs expect to allocate additional budget to business continuity planning, 55% say that they will invest more in security, compliance, and governance, with a further 52% expanding expenditure for cybersecurity technologies, policies, and practices.
Organisations intend to reinvent strategies to suit hybrid operating models: 58% plan fundamental overhauls, and 13% expect to spend more to succeed.
The financial imperative to mature security underpins the opportunity for business resilience. As organisations invest in counteracting risk, the CIO, CISO, and CRO can partner in the effort to drive integrated, technology-enabled security, compliance, risk, and governance outcomes.
Renewed funding also offers the organisation the prospect of retaining, retraining, and recruiting the muscle power required to keep pace with evolving security threats, regulatory directives, and technical requirements intrinsic in a remote-first world.
Embedding security in people is fundamental to maturing operational resilience. People-based obstacles occupy the top three blockers to evolving the organisation’s security posture. Overcoming organisational culture, addressing the talent gap, and improving awareness are, in order, the most crucial issues for local CISOs.
Almost seven in eight cybersecurity leaders contend with legacy mindsets when attempting to amplify the organisation’s security infrastructure and implement policies to secure information flows.
“Overcoming organisational culture is a perennial challenge for security leaders. It has been even more difficult in this virtual world,” observed ADAPT Director of Strategic Research Matt Boon.
The pandemic meant that 29% of organisations found it harder to raise awareness. We need to demystify security, make it appear less confronting, and align investment to key business priorities.”

Crisis-response compounds the need to refactor security awareness and augment resourcing. Local CISOs say that the pandemic created a new impetus to evolve how training is delivered.
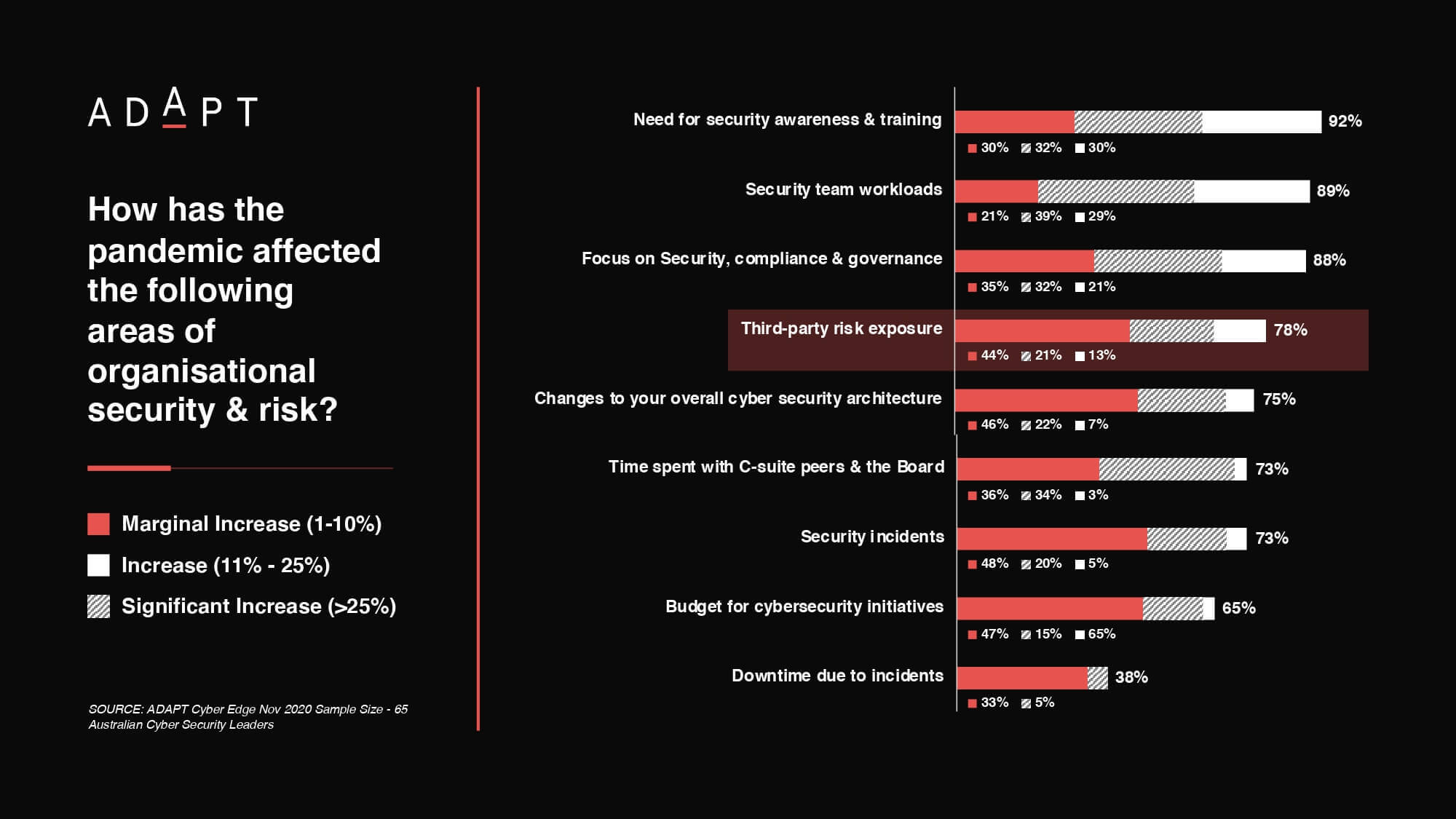
Whereas 92% of cybersecurity executives indicate that this is a crucial area for improvement, 30% expect to allocate significantly more attention to redesigning security awareness. The impact on security workloads throughout 2020 underscores the imperative to impart best practice across the organisation: 89% of security leaders indicate that their teams endured the effect of net-new and existing, amplified threats, with 29% facing increased demand of 25% or more.
Refactoring education into a modular, gamified, and domain-specific framework can help engage the workforce in a time and at a place that fits into their operational context.
Tapping into the analytic capabilities of existing staff may well help security leaders to:
- Mature organisational risk posture in operational, financial, and customer support areas
- Reduce the residual workload on the core security team by ameliorating existing threats
- Support the continuation of hybrid operations by reducing the risk of insider inattention
- Address the need to uplift the digital savviness of the top management team
CISOs invested in securing the hybrid perimeter are also grappling with a sponsorship disconnect. Though the top management team – the CEO and his or her direct reports – increasingly admire the CIO for their sure-handed digital-first response to the events of 2020, fully half of cybersecurity execs say that they lack the board-level buy-in.
Although the C-Suite may approve the overall concept of building a secure and trusted organisation, C-Level stakeholders’ indifference to the CISO’s granular initiatives may well stem from a lack of digital savviness.
Almost three in five cybersecurity leaders indicate that half or more of the board of directors are yet to accept digital technologies’ disruptive potential, even in this era of seismic change.
Implement a digital risk assessment to improve security line of sight
Organisations grappled with the existential risk of essential supplier failure in 2020. Although the operational threat posed by the sudden insolvency of a provider predated the pandemic, crisis-driven disruptions magnified both the likelihood and cascading impact of third-party vulnerabilities.
In addressing these systemic complexities, CISOs across the region grappled with an urgent need to evolve due diligence practices, get a better grip on forecast areas of exposure, and implement more robust mitigation strategies.
First, remake resiliency planning to incorporate impairments to backup operations. Although traditional business continuity assumes that disruptions will affect parts – not all – of a company’s operations, the interruptions endured in 2020 prevailed on a global scale. Organisations had planned for time-bound switchovers to secondary and tertiary failover sites to find these were also compromised.
Just 21% of cybersecurity leaders actuating crisis-response plans in the past twelve months felt that their ability to ensure business continuity remained very good. Consequently, security drills and disaster recovery planning need to assume diminished operational performance.
Second, invest in simplifying the effort to assess third-party risk. Organisations in Australia and New Zealand often grapple with complex, manual security processes: 81% struggle with a lack of workflow automation, whereas 58% plan to rationalise convoluted policies. Integrating and automating the verification of vendor assessments eases the identification of supply chain vulnerabilities.
By removing redundancy and pursuing administrative evolution, CISOs can quickly grasp variations to systemic risks and develop options to manage ongoing business impairment.
“Security professionals must consider their strategy for an environment dominated by an invisible perimeter,” advised ADAPT Senior Research Strategist Aparna Sundararajan.
It is challenging to control the security infrastructure of service providers. In some cases, companies have brought offshore contracts back in-house, as they posed a high risk in a lockdown environment.”
Third, amplify security infrastructure to defend against a rising set of attack vectors. In many cases, the race to remote meant that users were connecting into core systems over transmission pipelines that are less secure than those typically associated with internal private networks.
Consequently, the magnitude and frequency of security incidents have increased: 73% of cybersecurity executives deal with more frequent attacks; 25% endure increases of 11% or more.
CISOs seeking to augment security controls can:
- Implement multi-factor authentication to mitigate against digital identity breach
- Deploy behavioural analytics to defend against a socially-engineered attack
- Adopt security orchestration automation and response tools to prioritise incident response
Cybersecurity executives across the region rose to the challenge of remote operations in 2020.
CISOs rethinking organisational security should remake cybersecurity architectures to fit hybrid operations, embed security principles in people with domain-specific training, and implement digital risk assessments to forecast vulnerabilities in the supply chain more accurately.
Conclusion
Australia and New Zealand’s C-Suite drove a technology-first response to survive the disruptions endured in the nine months since March 2020. The region’s change-makers thereby demonstrated the potential of hybrid operating models to facilitate new pathways to innovate.
Business leaders seeking new avenues to growth can:
- Simplify internal workflows to remove legacy frictions from digital-first operating models
- Facilitate innovation by decoupling ideation from traditional temporal and physical anchors
- Inculcate the organisation’s trademark behaviours into new hires rapidly
- Knit together digital technologies to facilitate a seamless experience regardless of location
- Reimagine workforce engagement to foster innovative approaches to customer success
- Develop crisis-management success into strategic change-the-business credentials
- Redesign continuity planning to factor in impairments to backup operations
- Enable customers to quench their thirst for comfort via digital paths to expertise
- Actuate workforce creativity by refactoring talent management practices
- Build the foundation of the data-driven organisation by pursuing administrative evolution
- Remake cybersecurity architecture and infrastructure to address multi-cloud complexities
- Embrace modular architectures to modernise mission-critical workloads
- Refactor security awareness appropriate to user domain and technical proficiency
- Evaluate the requirement to claw back offshore contracts to reduce supply chain risk
An effective digital-first organisation is more than the sum of its technology parts. IT leaders can optimise digital workplace initiatives to enhance the human experience and showcase technology-fuelled innovations to the top management team to pursue growth.
Ultimately, by integrating focus and funding for technology-led change whilst also securing the invisible perimeter, the region’s changemakers can grasp the reigns of growth for success through 2021 and beyond.



























