Over half of critical infrastructure organisations fall short on basic controls like MFA and patching
ADAPT’s latest webinar “Know Your Customer: 2025 A/NZ CISO Insights” unpacked the voice of 132 security leaders across ANZ, including CISOs, security directors, and heads of governance.ADAPT’s latest webinar “Know Your Customer: 2025 A/NZ CISO Insights” unpacked the voice of 132 security leaders across ANZ, including CISOs, security directors, and heads of governance.
The organisations they represent contribute more than 18 percent of the country’s GDP and employ 7 percent of the national workforce.
CISOs are expected to protect their organisations from advanced threats, support transformation, and uphold regulatory requirements.
But many teams remain structurally underfunded, lack operational clarity, and continue to fall behind in baseline maturity.
This briefing, based on exclusive survey data presented at ADAPT’s April 2025 Security Edge event, reveals the immediate pressures facing security leaders and outlines the role vendors can play in addressing them.
The above video is only an excerpt.
ADAPT’s Research and Advisory Advantage clients can access the full webinar and slides.
Register to access the full webinar recording: Know Your Customer – 2025 A/NZ CISO Insights
Security leaders are being pulled into business growth with little support
CISOs are increasingly being asked to support business expansion, customer outcomes, and faster product delivery.
Gabby observed that this shift has brought more attention to identity and governance capabilities, which are viewed as essential enablers of scale.
At the same time, many CISOs report insufficient budget and staffing to deliver on these objectives.
Organisations focused on growth are often the ones most constrained by headcount and funding, creating a growing mismatch between strategic ambition and operational capacity.
Legacy systems block modernisation and transformation
Gabby said that while many CISOs want to support cloud migration and AI adoption, they are still tied to legacy systems and complex internal processes.
This limitation affects their ability to introduce advanced threat detection and implement modern security frameworks.
In highly regulated and operationally intensive sectors such as healthcare, policing, and utilities, the challenge is even greater.
Older platforms often lack visibility and flexibility, creating friction that delays security uplift and weakens response coordination.
AI risks are high and preparation is low
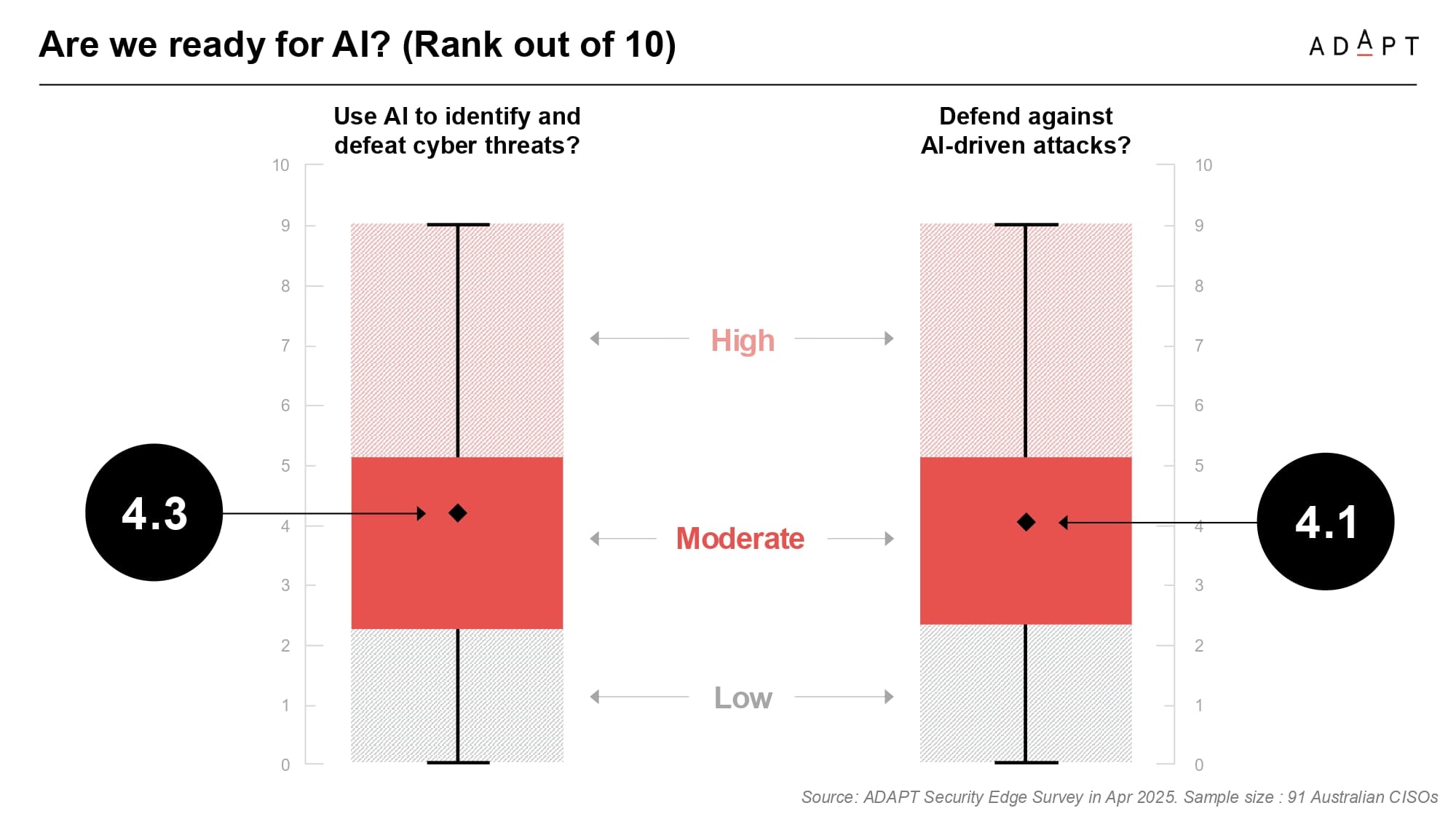
AI continues to gain momentum across organisations, but Gabby said security leaders do not feel ready to manage the risks.
Only 24 percent of CISOs say they are prepared to support AI adoption securely. The remaining 76 percent are either neutral or unprepared.
When asked to rate their capabilities, CISOs scored their ability to defend against AI threats at 4.1 out of 10, and their ability to use AI for security at 4.3.
Gabby explained that many teams are not implementing AI-based detection themselves and are unsure how to govern enterprise-wide use of generative models.
The perceived risk is highest in areas where AI makes autonomous decisions.
54 percent of CISOs view algorithmic decision-making as a critical risk, and 50 percent say the same for operations and process automation.
These concerns are driven by emerging attack vectors like prompt injection, data poisoning, and model supply chain compromise.
Tool fragmentation weakens response and limits speed
Gabby pointed to fragmentation as a major barrier to secure digital delivery.
The difference between high-performing and struggling teams often comes down to integration.
Among CISOs who believe security enables the pace of digital services, 60 percent have integrated tooling.
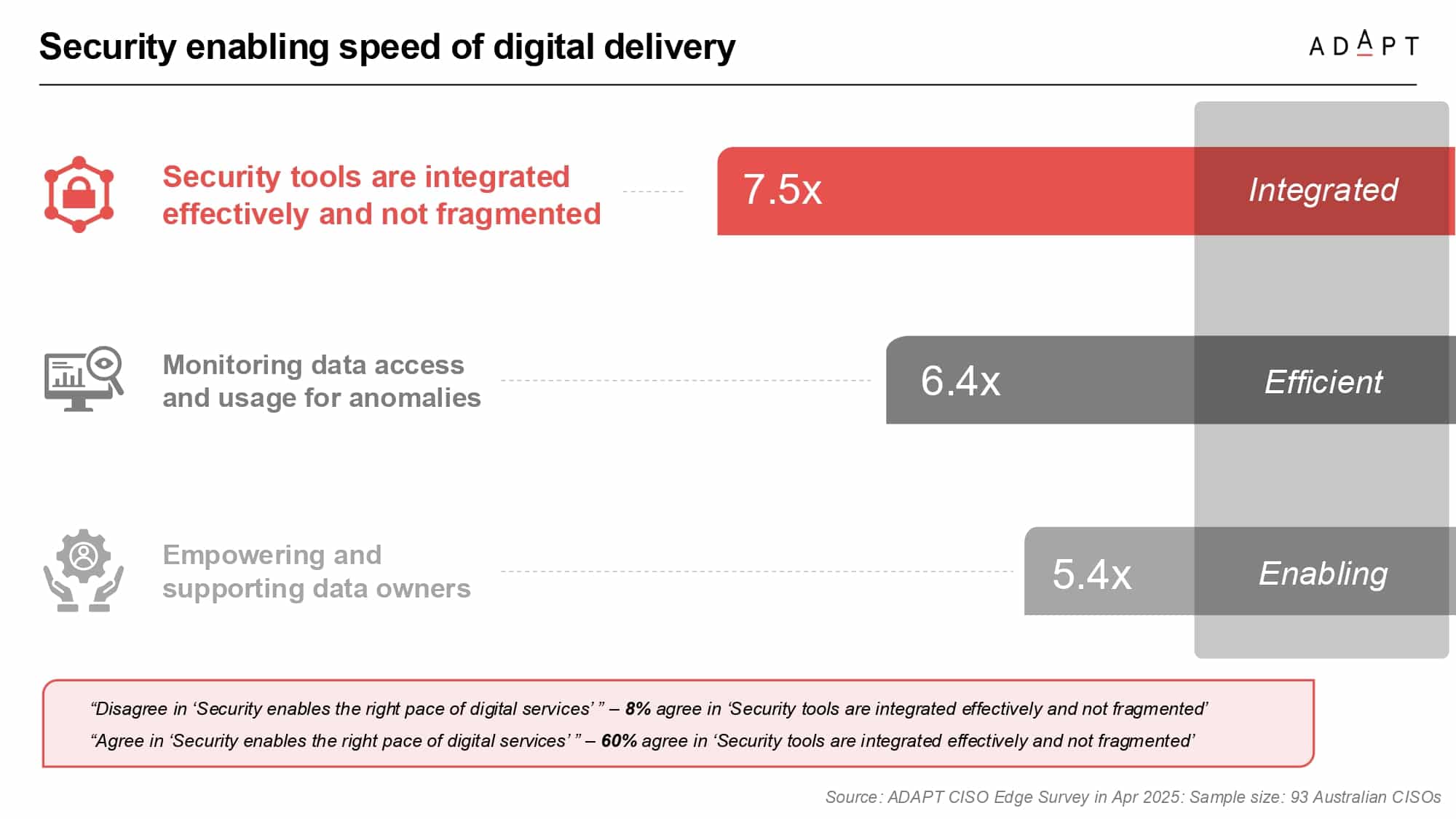
Among those who say it does not, only 8 percent have integration in place.
The most impactful factors for secure, fast delivery are consolidated tooling, anomaly detection, and empowered data ownership.
CISOs who report success in these areas are more likely to support iterative delivery and manage distributed risk environments without operational slowdown.
Maturity levels remain low across basic controls
ADAPT’s survey data shows that more than half of critical infrastructure organisations are not meeting baseline maturity across key control areas.
56 percent are below Level 2 on multi-factor authentication, 48 percent are below Level 2 on daily backups, and another 48 percent fall short on patching operating systems.
Gabby made clear that these are not advanced capabilities.
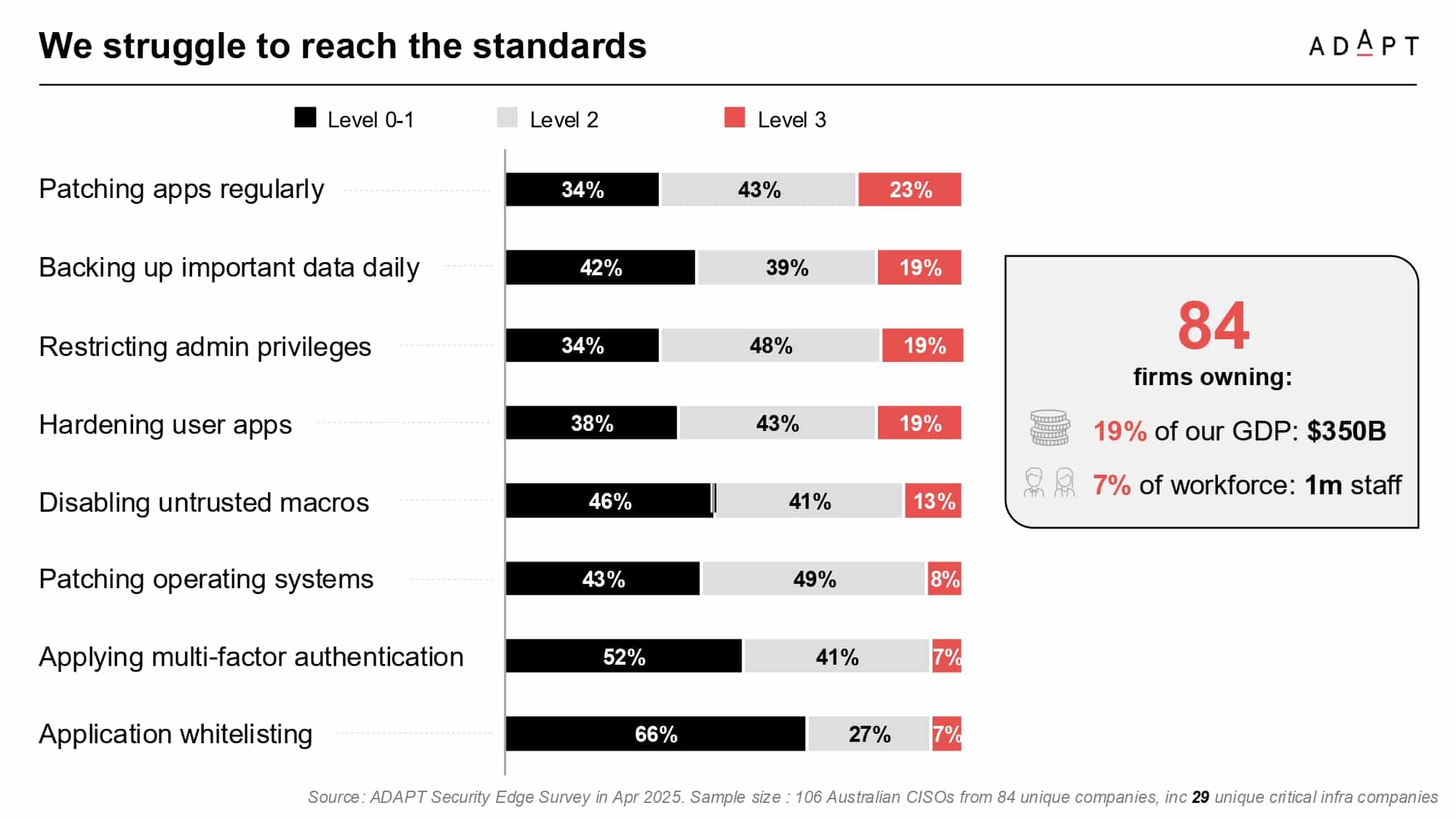
They are foundational measures required for baseline cyber hygiene and resilience.
Despite their scale and sectoral importance, many organisations still lack the tooling, processes, or internal advocacy to meet expected standards.
Recommended actions for tech vendors based on the insights
The 2025 data shows that most CISOs are under pressure to secure more with less.
While internal priorities evolve, expectations from executives and regulators continue to rise.
Vendors that want to stay relevant in this environment must shift from transactional outreach to targeted support based on local needs and practical delivery gaps.
- Use Australian examples and risk profiles to reflect the realities of this market. Relevance builds trust, and trust drives engagement.
- Provide tools, frameworks, and guidance that help CISOs manage AI-related risks and adoption securely across the business.
- Explain how your product reduces duplication, improves visibility, or replaces disconnected point tools.
- Equip CISOs with board-ready impact metrics, risk-reduction mappings, and financial justification content.
- Align your product with Essential Eight, ISO, or other maturity frameworks to help CISOs show progress and compliance.
- Show how your outsourced offering will operate with shared goals, transparent reporting, and cultural alignment.
- Acknowledge the shortage of internal security skills and bandwidth. Position your service or product to compensate for that gap without overpromising automation.
The role of the CISO is expanding in scope, but remains limited in capacity.
Many security leaders are responsible for enabling business growth, governing AI adoption, and reducing operational risk.
But most still lack the tools, visibility, and board-level support to deliver effectively.
The gap between responsibility and resourcing presents a clear opportunity.
Vendors that understand the local challenges and can provide measurable, integrated support will stand out.
The above video is only an excerpt.
ADAPT’s Research and Advisory Advantage clients can access the full webinar and slides.
Register to access the full webinar recording: Know Your Customer – 2025 A/NZ CISO Insights