Why Businesses Now Need A Chief Security Officer (CSO)
The threats that now confront organisations are progressively transcending both physical and technology domains.
Introduction
Traditionally, responsibility for protecting the business from external attacks has been assigned to specialist employees in different business units.
However, this segmented approach is becoming increasingly obsolete. The reality is that the threats that now confront organisations are progressively transcending both physical and technology domains.
Moreover, organisations have become dependent on technology in almost every facet of their operations. Even the provision of physical security now relies heavily on internet-enabled security functionality from devices such as sensors, cameras and electronic locking systems.
Businesses now need a new age Chief Security Officer (CSO) who can effectively oversee the convergence of physical security, business continuity and information technology security as well as associated responsibilities such as client privacy, fraud and third-party risk.
This is a very broad remit, and business leaders may have a concern that security generalists could be exposed if the organisation were to be targeted by skilled attackers with more specific talents.
However, ADAPT is increasingly hearing from Australian executives that they believe responsibility for cybersecurity should be a component within an overall corporate security function rather than being just a role within the IT department.
This reflects their appreciation that the exposure presented by cybersecurity incidents has much wider ramifications than just the uptime of their IT environment.
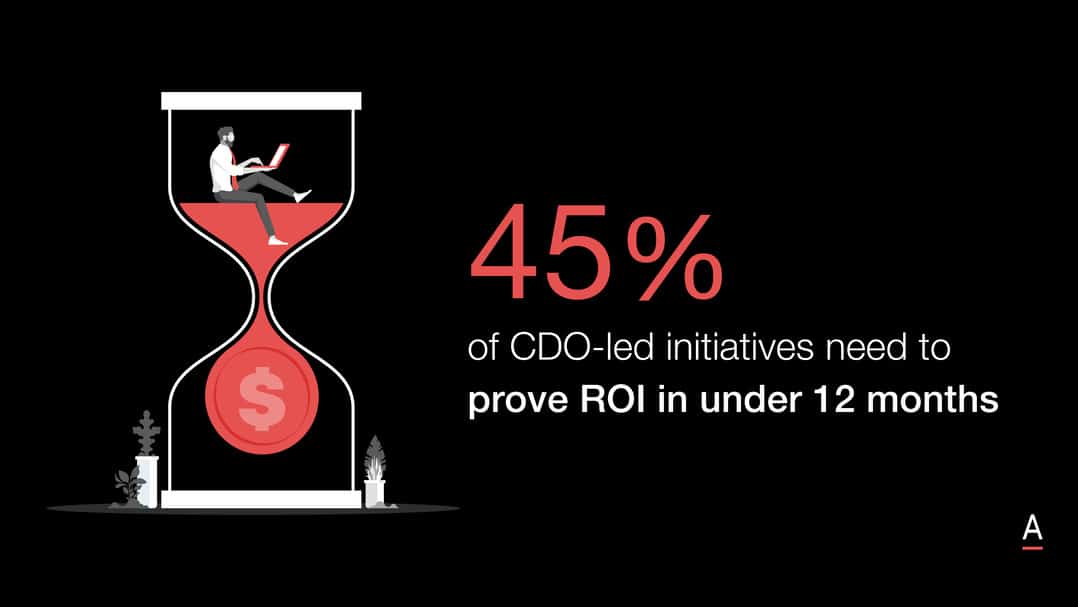
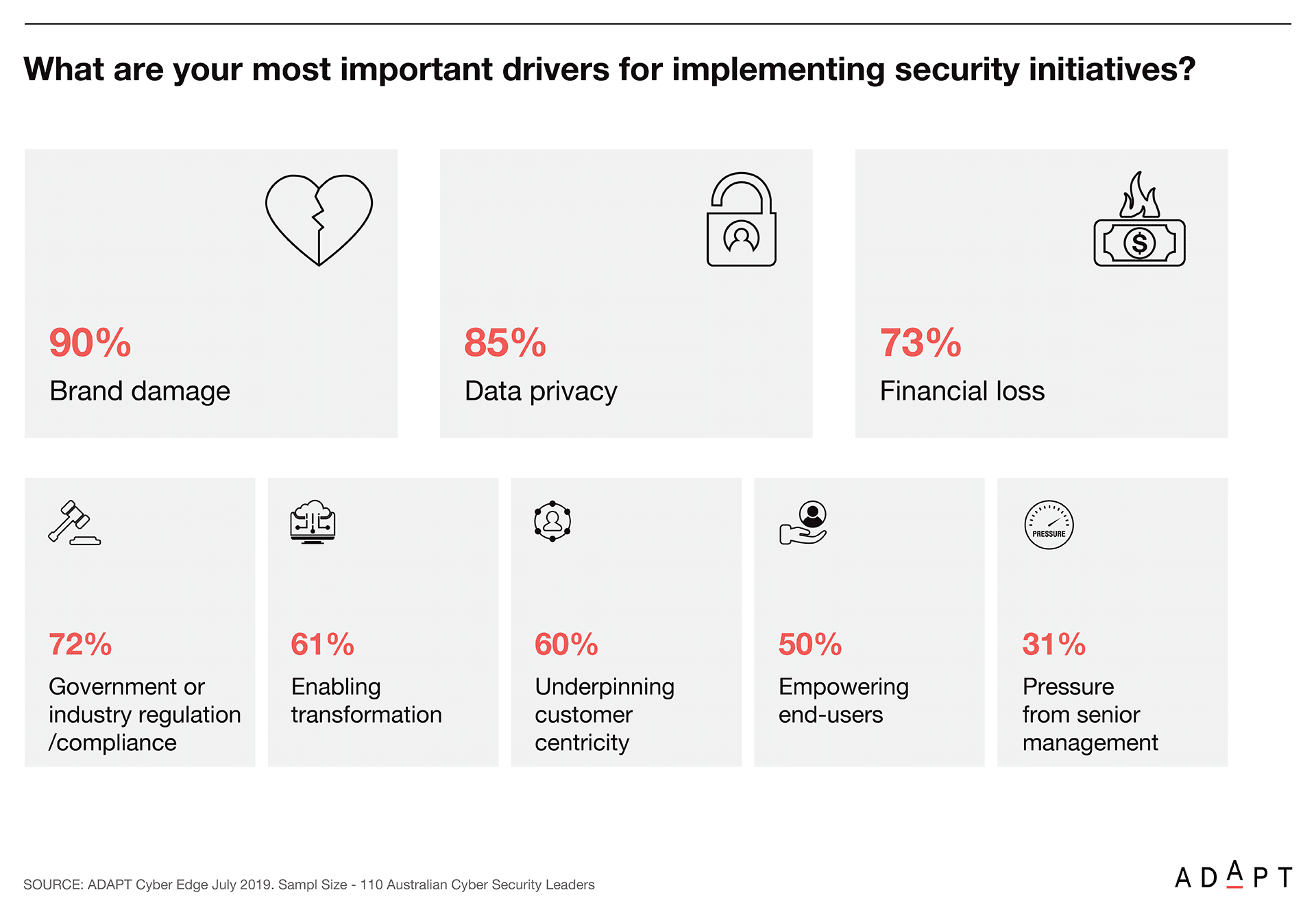
At ADAPT’s Security Edge, the latest cybersecurity research highlights that protecting the reputation of a brand, maintaining client data privacy and preventing financial losses are the key business drivers to implement security initiatives for any Chief Information Security Officer (CISO).
What you need to know
ADAPT’s research, conducted in July among delegates attending the 2019 CISO Edge event, revealed that 59% of CISOs scored ‘Organisational lack of security awareness’ as the biggest business inhibitor that confronted them.
Every year Australia’s businesses and government bodies spend around $21 billion on information security[1]. Yet, the evidence suggests that even this huge level of expenditure is failing to deliver the desired protection. According to Professor David Watts, from La Trobe University’s Law School, “There is no other area of public policy or social policy in Australia where such enormous costs are borne by the economy and where we seem to be less safe than more safe”.
Corporate security is becoming much more complex. It now requires an inter-disciplinary approach along with the collaboration of several traditionally independent business departments. Overseeing this effective interaction requires a forward-thinking and multi-talented CSO who is more of a leader who can direct others towards solving problems rather than a subject-matter expert.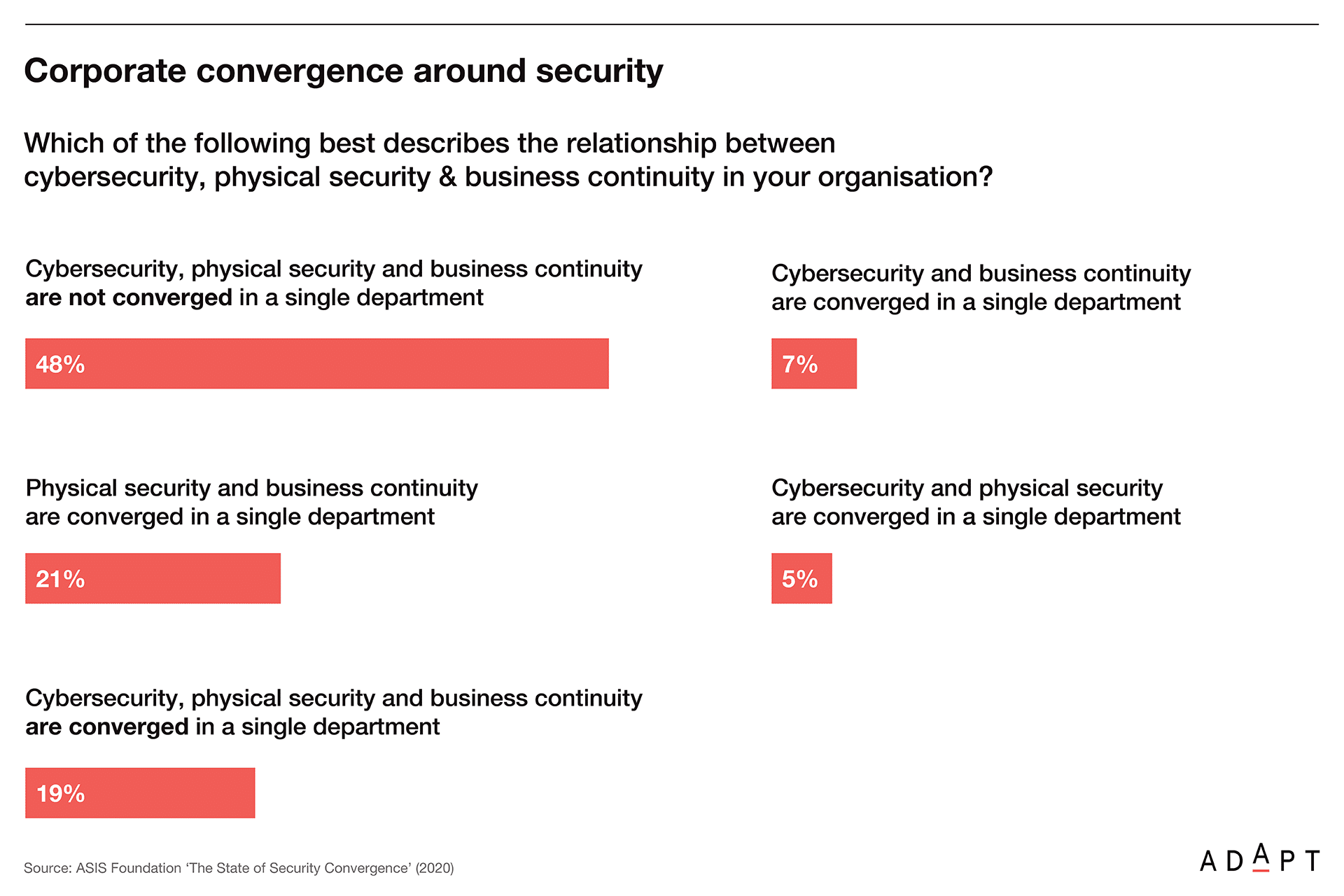
Yet, as the recently released study by the ASIS Foundation reveals (see below slide) that less than one-fifth of organisations say that they have a fully converged physical security, cybersecurity and business continuity function. More disturbingly, 70% of those that have not converged say they have no plans to do so.
A recent Business Insider Intelligence report predicts, that with the growing popularity of the Internet of Things (IoT) functionality, (as more and more computing moves to the network Edge), there will be 64 billion IP enabled devices in the world by 2025.[2] The reality is that this growth exacerbates the potential exposure of business to the threat of external attacks.
Dismantling the operational barriers between the teams focused on cybersecurity and on physical security will also reduce confusion over who has the task of tackling an emerging problem.”
However, the converged security operation will cover a wide scope of activity. In its early days, there is a likelihood of grey areas emerging where security team members may not fully appreciate where the accountability for problem resolution stops and starts.
As a converged security team requires people from different disciplines to work together, some could find, initially, that this experience is unsettling. This vulnerability could lead to ‘turf wars’ between team members as certain staff jostle to establish their authority.
What you need to do
Blended security threats require a more nuanced response by businesses. In this day and age it is unacceptable, where the threats that confront an organisation defy traditional corporate boundaries, to have multiple security departments operating in independent silos and only interacting together on an informal basis.
ADAPT emphasises that the security skillsets now needed by companies are an emerging and evolving requirement. It is unlikely that executives will find a mature, single framework for a converged security program. Instead, this will probably need to be custom-built by each organisation and aligned to its own specific security requirements.
The staff who populate a converged corporate security department will require a mix of practical skill sets that cross many security disciplines. It will be hard to find such employees. Even if they were available, hiring them would come at a premium. Therefore, organisations must accept the need to take responsibility for developing these multi-skilled security talents in their existing employees.
Several companies that are evolving into a converged corporate security function advocate the value businesses will gain by collaborating with local tertiary institutions in the development of the new-age security professionals that are needed.
Avoid the false belief that your organisation is solely responsible for tackling the security threats it faces. Consciously cultivate relationships with the Cybercrime teams in law enforcement and intelligence agencies. These organisations are usually the first to identify emerging security threats and patterns and can forewarn you of possible attacks.
Actively participate in industry security forums. This will help you refine the operations of a converged security department and expand your knowledge base about potential threats. In addition, these forums can provide real-life case studies of how your peers may have successfully responded to a particular security attack on their organisation.
The security vendors your organisation utilises will have extensive security experience. You should seek to avoid an adversarial approach to your engagement with these suppliers. They should be treated as part of your security team. They also have a vested interest in the success of your security operations.
How you need to do it
The calibre of the CSO selected to lead the new converged security team is of the utmost importance. These modern CSOs must create a new environment that fosters collaboration between staff members with markedly different skill-sets. They must also build the framework that enables these people to work together effectively. In addition, the CSO regularly needs to liaise with Board members, and the executive leadership, so they are fully informed about security matters.
To be on top of this broad range of matters the security team must be represented at the senior executive level. This should ensure that the implications of any major emerging threat to the business can be properly scrutinised. At the very least, the CSO should have a direct reporting line to the CEO.
Akin to any other form of insurance, developing effective corporate security requires the use of a risk-management approach. Assess and analyse the threats the business faces and determine the potential exposure if these risks were to eventuate. This assessment will establish a deeper understanding of what the business is required to invest to minimise this vulnerability.
Tailor the focus of the new department to the security priorities of the organisation. For example, mining companies attach great importance to the health and safety of their employees whilst financial organisations regard minimising fraud as one of their key metrics. There will not be one generic operating model for security that will work for everyone.
Ideally, the team members in a converged security department would be co-located. However, with most organisations having dispersed operations across cities and countries, most CSOs will face the challenge of making a virtual security team effective. Toolsets need to be selected to help foster this collaboration. These should not be imposed on the security department. Instead, they should be delegated the responsibility for selecting the product sets they want to use.
Nevertheless, most organisations will still need a security ‘nerve-centre’. This will house people with core skill-sets like architects, fraud investigators and cyber specialists. The role of this operation will be to create a situational awareness of security threats and incidents across the business as they are happening.
ADAPT recommends that this central operation should use Agile work practices such as daily stand-ups and an Agile wall of projects and activities to interact with the rest of the security team. This will help create regular, practical team engagement and help foster an esprit de corps among colleagues.
Utilising data analytics will be important. With a large workload and a broad remit, the challenge is to optimise the efficiency of the security team.
It will be ineffective to just throw people at problems. Instead, data analytics can help automate responses. The two priorities in the security team are time to detect and time to contain. Automation can help with both.”
Moreover, data analysis will highlight patterns of suspicious behaviour. This will enable the business to nip problems in the bud and better direct security personnel to the challenges at hand. For example, one executive told delegates at an ADAPT Edge event that the data scientists in a security team he led had created a model which provided the business with predictive fraud indicators.
The Bottom Line
Like any major change management task creating a new converged security culture will take time. People who are familiar with the traditional way of doing things need to understand the reasons for these changes.
Moreover, they probably do not regard those working in other security disciplines as their peers. They could even be dismissive of the importance of their core security competencies. It will be counterproductive to try and smash a new converged business security team together.
The objective is to get it right. Executives should expect that this will take time. One aspect of this will be a series of small-group conversations with different security employees to explain the rationale for the change.
It is probable that during this dialogue some staff will express concerns or doubts. These need to be heard and addressed. Even when the group is launched its operations will be something of a work in progress.
It would be a surprise if everything worked as needed from the outset. Instead, the operations will need to be adjusted and fine-tuned based on what is learnt and how it is working in practice.
The advice given to ADAPT by those actively converging their security operations is the benefits that will be derived from doing this have more to do with operational effectiveness rather than cost savings or efficiencies. These benefits include:
- A better alignment of security strategy with corporate goals,
- The establishment of a shared set of practices and goals across all security disciplines,
- The development of multi-skilled specialists more appropriate for the security needs of modern business and
- The elevation of security matters so their importance and potential impact are better appreciated by the C-suite and Board of Directors.
A converged security practice will ultimately create a whole that is greater than the sum of its parts. In effect, the business will have more eyes on the threats that confront them.
Furthermore, these employees will have a wider perspective on these matters, giving them a greater capability to tackle the constantly evolving threats that confront the business. This heightened security culture will also generate a greater appreciation of the risks the business faces.
Some advocates even claim that once it is bedded down, a converged security operation has the potential to offer a significant competitive advantage.
The argument is that if one organisation can repel and recover from an attack on its operations better than its competitors, then this is likely to be reflected in it achieving longer uptime, enhanced customer satisfaction, more sales and greater employee productivity.
However, perhaps the greatest advantage a converged security practice can achieve is boosting the confidence of others in the business. The multi-disciplined security team will better protect the organisation’s key assets and help them get back up and running faster if something disruptive occurs.
In addition, the presence of a converged security team avoids any finger-pointing between different security practices if responsibility for overcoming a security incident were to be questioned.
As one executive advised delegates at ADAPT’s CISO Edge conference last year, “When it comes to security all the business wants is one throat to choke”.
[1] https://ia.acs.org.au/article/2019/australia-wastes-its-cyber-spending.html
[2] Business Insider ‘IoT report: How IoT technology growth is reaching mainstream companies’ (2019)